GLOBAL KNOWLEDGE NETWORKä CERTIFICATION PRESS |
Chapter 1
Introduction to Internetworking
Certification Objectives
*Network Evolution
*The OSI Model
*Encapsulation
*DIX and 802.3 Ethernet
*802.5 Token Ring
*ANSI FDDI
*MAC Addresses
*Interfaces
*RS-232
*Signal Sent on that pin
*V.35
*HSSI
*BRI Interfaces
*Network Clock
*From the Classroom
*Setting Up a Lab Network
*Wide Area Network Services
*Point to Point
*Frame Relay
*X.25
*ISDN
*ATM
*Layer 3 Addresses
*Routed Protocols vs. Routing Protocols
*Routing Algorithms and Metrics
*Reliability
*Windowing
*
![]()
Cisco Certified Internetworking Engineers, or CCIEs, are recognized as some of the premiere internetworking professionals in the information systems industry. Their understanding of the intricacies of internetwork design and architecture stems from both dedicated study and experience. The following skills are required to attain the highest level of certification, the CCIE.
To start you on your certification path, this book provides you with the information needed to become a Certified Cisco Network Associate (CCNA). A potential CCNA must have the knowledge to install, configure, and operate simple-routed LAN, routed WAN, and switched LAN and LANE networks.
This is the beginning of an adventure in knowledge. What this book can offer as both a reference and a learning tool can take an engineer to the heights of an internetworking career.
The Internetworking Model
There is a distinction made between networking and internetworking. Networking is the process and methodology applied to connecting multiple computers so that they are able to exchange information. Internetworking is the process and methodology applied to connecting multiple networks, regardless of their physical topologies and distance. Internetworking has evolved with the rapid growth and change in networking. Because of this, the basic building blocks and reference models for networking are also used and applied to internetworking.
Internetworks evolved from necessity. In the early days of computing (the 1950s and 1960s), internetworks did not exist. Computers were autonomous and proprietary. In the late 1960s, however, the United States Department of Defense (DOD), became interested in academic research being done on a packet-switched wide area network design. "Packet" referred to a small bundle of data. "Switched" referred to the use of a routing system similar to the switch-based telephone system. And "wide area network" (WAN) meant that the network would extend over sites that were physically distant from each other.
DOD wanted to use this technology for national defense, as a means to share radar data, and distribute control and commands in the case of a nuclear war. The agency within DOD that handled the network research was the Advanced Research Projects Agency (ARPA), which later prefixed "Defense" to the beginning of their name and became known as DARPA.
{Answer to Self Test Question #1}The DARPA project included scientists and engineers from universities and the Bolt, Baranek and Newman company of Massachusetts, who faced the two challenges in this project: interconnectivity and interoperability.{Answer to Self Test Question #2}
The result of the DARPA project was ARPANET, which eventually became the Internet, and the evolution of the IP protocol suite, which was then included as part of Berkeley's version of UNIX. ARPANET grew into the Internet by including networks in other government and university campuses. And that grew even further with the inclusion of commercial enterprise networks.Networks did not become prevalent in corporations until the 1980s when the personal computer (PC) became popular. After companies realized that sharing hard disk space on some of the earliest file servers enabled employees to share data easily and further boosted productivity, they implemented networks on a large scale. They created LANs (Local Area Networks) and then connected them into WANs (Wide Area Networks). After the Internet went commercial in the early 1990's, corporations began to connect to it as well.
There are two standards to consider in internetworking: de jure, and de facto. De jure means by right or legal establishment. De facto means established by actual fact, though not officially or legally recognized. The evolution of TCP/IP created a de facto standard for that protocol, because it grew and became accepted, although it was not proposed as a standard until after its wide acceptance.
{Answer to Self Test Question #3}{Answer to Self Test Question #22}The OSI (Open Systems Interconnection) reference model is a de jure standard.The International Organization for Standardization (ISO) created the OSI model and released it in 1984 in order to provide a network model for vendors such that their products would interoperate on networks. The OSI reference model provides a hierarchical tool for understanding networking technology, as well as a basis for current and future network developments.
This model also takes into account the interconnectivity and interoperability challenges faced by the DARPA project engineers. The way that the OSI model answered these challenges was through a seven-layer protocol suite model, illustrated in Figure 1-1. By dividing the model into layers, the capability to interoperate and interconnect became manageable, since each layer was self-contained, not relying on the operating system or other factors.
{Answer to Self Test Question #23} The layered approach benefited vendors, too, since they only needed to concentrate development efforts on the layers that their own product used, and could rely on the existing protocols at other layers. Not only are development costs kept to a minimum, but marketability is increased, since the product works with other vendors' products.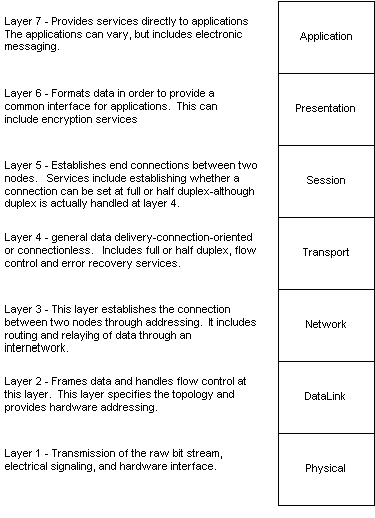
Figure 1 OSI reference model
The model describes how each layer communicates with a corresponding layer on the other node. Figure 1-2 illustrates how data works its way through a network. At the first node, the end user creates some data to be sent to the other node, such as an e-mail.
{Answer to Self Test Question #4}{Answer to Self Test Question #24}At the application layer, an application header is added to the data. The presentation layer adds its own header to the data received from the application layer. Each layer adds its own header to the data received from the layer above. However, at lower layers, the data is broken up into smaller units and headers added to each of the units. For instance, the transport layer will have smaller datagrams, the network layer will have packets, and the data link layer will have frames. The physical layer handles the data in a raw bitstream. When this bitstream is received at the destination, the data is reassembled at each layer, and the headers of each layer discarded, until the e-mail is readable by the end user.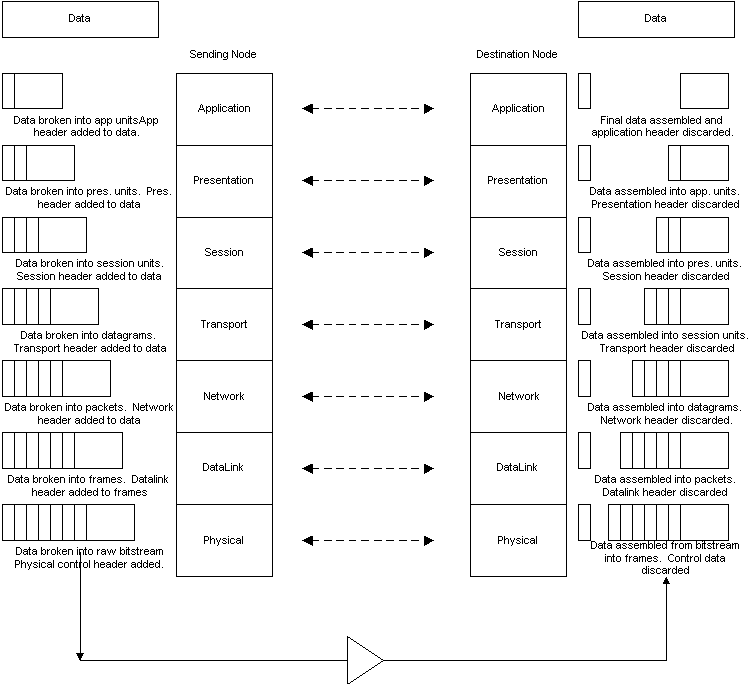
Figure 2 How the OSI model transports data
A common mnemonic device for remembering the layers (application, presentation, session, transport, network, data link, physical) in the right order is All People Seem To Need Data Processing.
{Answer to Self Test Question #5}
Encapsulation is the process of adding a header to the data, or wrapping the data. In order to send data out on a Token Ring network, the data must be wrapped with the Token Ring header before it is transmitted.{Answer to Self Test Question #25} The terms wrapping and encapsulation refer to both the header and the ending bits that are added to each bundle of data. Header bits are used to signify the beginning of a data bundle, and frequently include addressing and other features, depending on the protocol and layer. The ending bits are typically used for error checking. Header bits receive more attention, since they include most of the protocol feature implementation.Encapsulation may occur at each layer in the OSI reference model. The entire packet from each layer is inserted into the data field of the next layer, and another header is added. Occasionally a layer splits the data unit (including previous layer header) into multiple, smaller data units, and each one of the smaller units is wrapped with a new header from the lower protocol layer. This process helps control data flow and addresses packet size limitations on the network. As the data moves down the model, it becomes smaller and more uniform in size and content.
When data is received, the corresponding layer at the receiving node reassembles the data field before passing it to the next layer. As the data moves back up the model at the destination, it is pieced back together like a puzzle.
Physical and Data Link Layers
{Answer to Self Test Question #6}
The physical layer, or layer 1, defines the actual mechanical specifications and electrical data bitstream. This includes the voltage level, the voltage changes, and the definition of which voltage level is a "1" and which is a "0." The data rate of transmission, the maximum distances and even physical connectors are all included in this level.The data link layer, or layer 2, is also known as the link layer. It consists of two sublayers, the upper level being the Logical Link Control (LLC), and the lower level being the Media Access Control (MAC). Hardware addresses are actually MAC addresses in the data link layer. The physical address is placed here, since the physical layer handles only raw bitstream functions.
{Answer to Self Test Question #27} The data is broken into small "frames" at this layer.The physical and data link layers are usually implemented together in hardware/software combination solutions. Examples include hubs, switches and network adapters, and their applicable software drivers, as well as the media or cables used to connect the network nodes.
{Answer to Self Test Question #26} The remaining layers are usually implemented in software only.{Answer to Self Test Question #7}
The IEEE (Institute for Electrical and Electronics Engineers) created several standards under the 802 series. Table 1-1 describes the 802 series of standards that are currently in existence or are still being developed.|
Standard |
Description |
|
802.2 |
Defines LLC protocol that other 802 standards can use |
|
802.3 |
Ethernet (CSMA/CD) |
|
802.3u |
Fast Ethernet 100BaseT |
|
802.4 |
Token Bus (rarely used) |
|
802.5 |
Token Ring |
|
802.6 |
MANs (Metropolitan Area Network) using two fiber-optic buses in opposing directions |
|
802.9 |
Isochronous Ethernet - channel sharing between one async channel and 96 dedicated channels providing 16 Mbps |
|
802.11 |
Wireless LANs using CSMA/CA (Carrier Sense Multiple Access/Collision Avoidance) |
|
802.12 |
100VG-AnyLAN |
Table 1 IEEE 802 Standards Series
{Answer to Self Test Question #8}
Digital, Intel and Xerox (collectively known as DIX) created Ethernet in the 1970s. This was used as the basis for the IEEE 802.3 standard released in 1980. DIX then updated their standard to match the IEEE 802.3 version. The term Ethernet is commonly used to refer to either one of these network standards.However, Ethernet and IEEE 802.3 do have some differences. One difference is that 802.3 specifies the physical layer and the MAC portion of the data link layer, while DIX Ethernet specifies the entire physical and data link layers. 802.3 specifies different physical layers, but DIX Ethernet only specifies one. Table 1-2 compares the two standards.
|
|
DIX |
IEEE 802.3 Physical Standards |
|||||
|
|
Ethernet |
10BaseF |
1Base5 |
10Broad36 |
10Base2 |
10Base5 |
10BaseT |
Rate Mbps |
10 |
10 |
1 |
10 |
10 |
10 |
10 |
|
Topology |
Bus |
Star |
Star |
Bus |
Bus |
Bus |
Star |
|
Media |
50-ohm thick coaxial |
Fiber-optic cable |
Unshielded twisted-pair |
75-ohm coaxial |
50-ohm thin coaxial |
50-ohm thick coaxial |
Unshielded twisted-pair |
Table 2 Physical Layer Specifications for IEEE 802.3 and DIX Ethernet
{Answer to Self Test Question #9}
Ethernet uses a carrier sense multiple access/collision detection (CSMA/CD) method. In the CSMA/CD network, nodes can access the network any time they have data to send. Before a node transmits data, it "listens" to see if the network is busy. If not, the node transmits data. If the network is in use, the node waits.{Answer to Self Test Question #28} Collisions occur if two nodes listen, hear nothing and then access the wire simultaneously. This ruins both transmissions, and both stations have to try a second time. {Answer to Self Test Question #10}There is a backoff algorithm that creates a random wait time for retransmissions so that a second collision will not occur. Figure 1-3 illustrates this process.
Figure 3 Collisions on CSMA/CD network
Ethernet, including 802.3, is a broadcast system.{Answer to Self Test Question #29} That means that all nodes see all data frames, whether or not that data is meant to be received by that node. Each node examines the frame header addresses as the frames are received to determine if they are destined for that node. If not, the frames are forwarded on the network. If they are destined for the node, it passes them to the upper-level protocols for processing.
{Answer to Self Test Question #30}
The IEEE 802.3 frame, shown in Figure 1-4, begins with a preamble of alternating ones and zeroes that tells the receiving station that this is a new frame. The next byte is a start-of-frame delimiter (SOF) that ends with two consecutive one bits. The next part of the frame header is the destination and source address fields. An address consists of three bytes identifying the vendor, and a second three bytes that are specified by the vendor. After the source address, in IEEE 802.3 frames, there is a two-byte field that discloses the number of bytes of data contained within the frame. The data itself is next, at a minimum of 64 bytes (padded with extra bytes if it is too short), and finally the four-byte FCS field (Frame Check Sequence) ends the frame.{Answer to Self Test Question #31}The FCS field includes a cyclic redundancy check (CRC) value that is used to check for damage that may have happened to the data during transmission.
Figure 4 IEEE 802.3 frame format
{Answer to Self Test Question #11}
Token Ring networks were originally a proprietary network specification created by IBM in the 1970s. Token Ring networks are nearly identical and compatible with the IEEE 802.5 specification developed later, which was based on IBM's Token Ring. The differences include:The main concepts of Token Ring are described in its name. It is a token-passing network that connects nodes in a logical ring topology. Token passing (illustrated in Figure 1-5) uses a small, specially formatted frame, called a token, which is passed from node to node on the ring.
{Answer to Self Test Question #32} When a node possesses the token, it is granted transmission rights. If there is nothing to transmit, the node sends the token on to the next node.{Answer to Self Test Question #33} When a node does have information to transmit, it flips one bit of the token and turns it into a start-of-frame field, then appends the data and forwards it on. Unless "early token release" is used, the node retains the token until the data frame travels around the ring back to the sender. The data follows the ring until it reaches the destination node, which copies the data. The data frame goes back to the sending station, where the originator can check whether the data transmission was successful.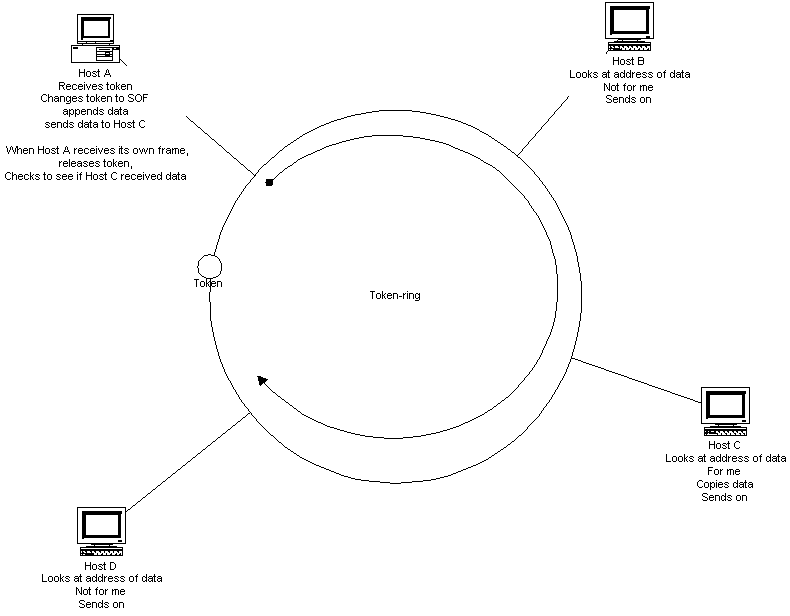
Figure 5 Token passing
There is also a method for token-seizing, (or access priority) in Token Ring, whereby priority can be assigned to stations so that they can use the network more frequently. A station with equal or higher priority than the priority value contained in a token can seize it for its use. In doing so, it raises the token's priority, and returns it to the original priority on the next pass.
{Answer to Self Test Question #12}
Beaconing is a Token Ring mechanism that detects network faults. If a station detects a failure in the network, it sends a beacon frame, which specifies the reporting station, its nearest active upstream neighbor (NAUN), and the failure area. Beaconing triggers autoreconfiguration, in which the network nodes attempt to reconfigure the network around the failed areas. A multistation access unit (MSAU) may "wrap" a port so that it is not part of the ring, bypassing all inactive or nonfunctional ports, but including all active, functioning ones.{Answer to Self Test Question #13}
There are two types of frames, a token and a data frame. A token (shown in Figure 1-6) is three bytes long. A data frame (shown in Figure 1-7) consists of the data sent by upper-layer protocols and the Token Ring header. There is a special data frame called a MAC frame, for commands that consist of Token Ring control information and header.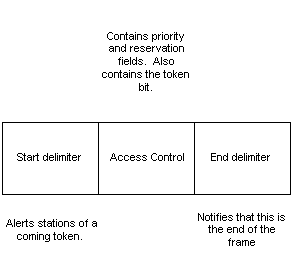
Figure 6 Token Ring token format

Figure 7 Token Ring data frame format
In the mid 1980s, ANSI (American National Standards Institute) X3T9.5 standards committee created FDDI (Fiber Distributed Data Interface), which was developed to address the growing bandwidth needs in network systems. ANSI submitted FDDI to the International Organization for Standardization, which then created a compatible FDDI standard.
{Answer to Self Test Question #14}The FDDI standard specifies the physical and MAC portion of the data link layers for a token-passing, dual-ring topology using fiber-optic media at 100 Mbps. Fiber has some advantages over copper wire.The MAC layer specification defines the media access method, frame format, token passing method, MAC addressing, CRC (cyclic redundancy check), and error recovery. The physical layer specification defines the data framing, clocking requirements, and transmission media (bit error rates, optical components, fiber-optic connector, power levels). Also, FDDI provides for the station configuration, insertion, removal, fault recovery, ring configuration and control.
In the dual ring configuration, traffic travels in one direction on one ring, and the other direction on the other ring. One ring is primary, and used for data transmission. The other is secondary, and used for backup. Class B stations attach to a single ring through a concentrator so that rebooting a station will not bring down the ring. Class B stations are known as SAS (single-attached stations). Class A stations attach to both rings, and are known as DAS (dual-attached stations).
{Answer to Self Test Question #34} The dual ring provides fault tolerance, as shown in Figure 1-8. If a Class A station on the dual ring fails, it creates a ring failure. During that failure, stations on either side of the fault wrap their ports, restoring service through the backup ring. If there is more than one break in the ring, multiple separate rings can be the result.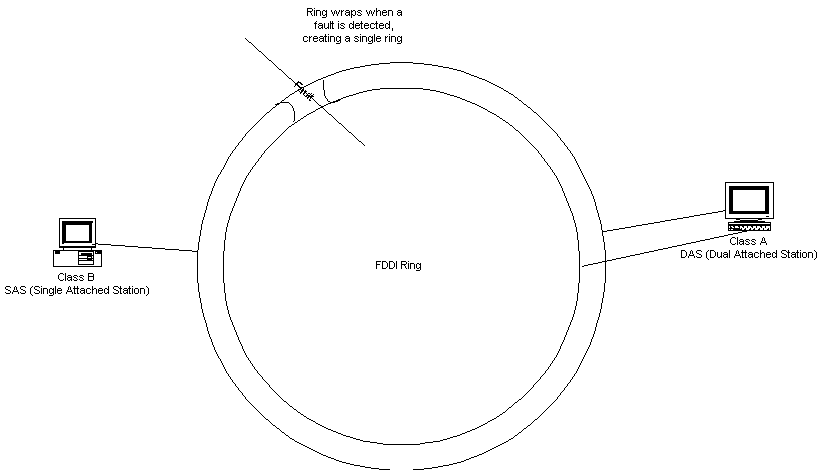
Figure 8 Dual Ring fault tolerance
FDDI supports both asynchronous and synchronous traffic. Synchronous is allocated a portion of the bandwidth for stations requiring continuous transmission; asynchronous is allocated the remainder. Stations using the asynchronous portion are assigned priority from a priority scheme of 8 levels, which are shown in Figure 1-9.

Figure 9 FDDI frame format
The data link layer consists of two sublayers: Logical Link Control (LLC) and Media Access Control (MAC). The MAC sublayer determines the address for the hardware at that layer.
{Answer to Self Test Question #35} This address is network independent, such that wherever the hardware is "plugged in" to the internetwork, it would have the same MAC address, regardless of the network address. The vendor usually assigns the MAC address. In the Ethernet scheme, a series of Ethernet MAC addresses are assigned to a vendor, who then assigns a different address to each interface produced. An Ethernet MAC address consists of 12 digits. The first six digits (the Organizationally Unique Identifier, or OUI) are the unique number assigned to the vendor by the IEEE, and the remaining six digits are the series. As a result, each network interface card will have a different MAC address on any given LAN or WAN.The physical layer encompasses several different types of interfaces. These are either dictated by the protocol used on the segment, or by the proprietary specification of the vendor. Interfaces are used to connect data terminal equipment (DTE) and data circuit-terminating equipment (DCE) devices. DTEs are network nodes such as routers and servers. DCEs are internetworking devices, such as packet switches, generally owned by the carrier, which provide clocking and switching.
{Answer to Self Test Question #15}
RS-232 is the EIA (Electronics Industries Alliance) serial port interface standard. In the RS-232 serial port, one pin is used to transmit data, another to receive data. The remaining pins are used to establish and maintain communication between two serial devices. There is both a 25-pin (DB-25) and a 9-pin (DB-9) version. The cable media must be configured so that each wire transmits or receives the type of data expected. RS-232 cables, which are rated to 19.2 Kbps, must be configured to properly connect DCE and DTE devices. Unique pinouts are required for cables that do not conform to the standard. The pinouts are described in Table 1-3.|
9 Pin |
25 Pin |
Symbol |
Input/Output data |
|
|
- |
1 |
|
Protective Ground |
|
|
3 |
2 |
TX |
Transmit data |
Output |
|
2 |
3 |
RX |
Receive data |
Input |
|
7 |
4 |
RTS |
Request to send |
Output |
|
8 |
5 |
CTS |
Clear to send |
Input |
|
6 |
6 |
DSR |
Data set ready |
Input |
|
5 |
7 |
|
Signal Ground |
|
|
1 |
8 |
DCD |
Data Carrier Detect |
Input |
|
- |
9 |
|
Transmit Current Loop + |
Output |
|
- |
11 |
|
Transmit Current Loop - |
Output |
|
- |
18 |
|
Receive Current Loop + |
Input |
|
4 |
20 |
DTR |
Data Terminal Ready |
Output |
|
9 |
22 |
RI |
Ring Indicator |
Input |
|
- |
23 |
|
Data Signal Rate Indicator |
Input and Output |
|
- |
25 |
|
Receive Current Loop - |
Input |
Table 3 RS-232 Pinouts
ITU-T (International Telecommunication Union - Telecommunication Standardization Sector) created an entire V.xx series of standards. The V.35 standard is a physical layer protocol suitable for connections to a packet network at speeds up to 48 Kbps, and beyond, even to 4 Mbps. This standard specifies synchronous communication.
Both the ISO and the ITU-T are currently reviewing HSSI (High Speed Serial Interface) for standardization. HSSI is a DTE/DCE interface that handles high-speed communication over WAN links. {Answer to Self Test Question #16}This is a physical layer specification of a point-to-point connection that runs at speeds up to 52 Mbps using shielded twisted-pair copper wire.
{Answer to Self Test Question #36}
BRI (Basic Rate Interface) is an ISDN (Integrated Services Digital Network) term for an ISDN connection consisting of two B channels at 64 Kbps and one D channel at 16 Kbps. A terminal adapter is a modem-like device used to connect the DTE device to the ISDN circuit. The ITU-T's BRI standard specification for the physical layer includes data transmission for the B channels and signaling, framing control, and other overhead control information on the D channel.{Answer to Self Test Question #37}
Synchronizing network timing is handled at the physical layer of the OSI reference model. This clocking of the network bitstream can improve throughput, and is mandatory for WAN circuits. Specifications for clocking are included in the framing format and control mechanisms defined in interface standards.This is a long chapter, filled with dry information about abstract concepts. In the ICRC classes, this material used to take the better part of the first day. The students were always frustrated, because their primary motivation in coming to class in the first place was to get their hands on some actual routers! One of the things we used to do to help break up the tedium of non-stop lectures was to have the students help cable up the classroom network. In contrast to the course's focus on layer 3, with a little about layer 2, putting the equipment together into a network is purely a physical layer activity. I'd like to walk you through some of the considerations for setting up a classroom or a lab network, in case you need to set up one of your own someday.
The classroom network uses a combination of Ethernet and serial connections. The Ethernet connections are simple to set up, but there are still a few items to pay attention to. In the past, Cisco made no assumptions as to which Ethernet media the customer would use, so the interface provided on the older products is AUI only. This interface is useful for a 10Base5 network, but most customers use 10Base2 or 10Base-T, both of which require a transceiver to be attached to the AUI interface to convert the signal and make the physical connection to the network cable.
Newer Cisco products provide a dual-media interface for Ethernet, which you can recognize by the RJ-45 receptacle for a 10Base-T cable alongside an AUI interface. Cisco is not giving you two Ethernets for the price of one here; you can use one or the other, but not both simultaneously. The trick with this one is that the default media type for this interface is AUI, which is probably not the one you want! You will need to configure the router interface explicitly to use the RJ-45 connector. The command to use is media-type 10baset.
In most production networks, the serial interfaces would connect the router to a CSU/DSU, which would connect to a WAN service provider's network. The router would be a DTE device and would take a clock signal for that line from the provider's network clock. In the lab there's no provider to give us a clock signal, and there's no CSU/DSU. You will need to do two things to accommodate these differences in order to make the serial connections work in the lab: use back-to-back cable pairs, and configure a clock rate in the router.
Serial interfaces on most Cisco routers use a DB-60 high-density connector on the router end. The cables are called transition cables because the non-router end determines its electrical signaling. These might be EIA/TIA-232, V.35, X.21 or RS-449. In a production network, the cable you would buy to connect to your CSU/DSU would most likely be a male DTE V.35 cable. If we are making a connection between two routers in the lab, however, there won't be a CSU/DSU, so the male cable will need to connect to a female DCE cable of the same signaling type in a back-to-back arrangement.
Now we have a connection made, but the router needs to get clocking for those connections from somewhere, since we don't have a provider's network to take it from. In the lab, you need to configure one end-the DCE end only-of each serial connection with a clock rate, which will dictate the speed at which the connection will transfer data. Use the clock rate command for this. The maximum clock rate you can specify will depend on the cable you are using. The V.35 cable will allow a clock rate up to 4 Mbps, while the EIA/TIA-232 will allow only 128 Kbps. You don't need to configure a clock rate on the DTE end of the connection.
A last word about serial cables: Cisco cables list for $100 apiece, so if you are using serial connections in your lab, you will need a $200 cable pair for each one. You might think that you're getting a rugged product for that price, but you're not. There are two pitfalls here: folded pins and upside-down cable attachments. The DB-60 high-density connectors are extremely delicate and the pins will fold up inside very easily if you're careless, ruining the cable. Be sure to watch the orientation of your cables with respect to the router interface before you attach them! The 60 pins are arranged in a matrix with four identical rows of 15 pins each, and the metal sleeve of the D-connector is thin and pliable, so you can physically attach the cable to the router upside-down without noticing it. It won't work this way, of course, so you may be in for hours of futile troubleshooting before you discover the problem.
-Pamela Forsyth, CCIE, CCSI, CNX
WAN services are networks in their own right, just without workstations connected to the link between the two networks. Figure 1-10 shows a WAN link. The purpose of a WAN connection is to be able to transmit data between two distant networks as efficiently as possible. The more efficient the link, the more transparent the connection to the end users. WAN links are typically slower than LAN links. For example, a T-1 is 1.544 Mbps, while Ethernet 10BaseT is 10 Mbps.
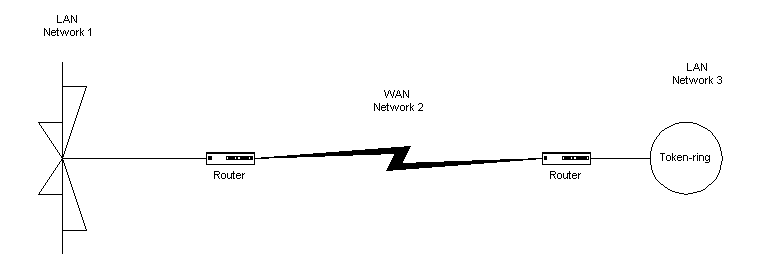
Figure 10 Two LANs connected by a WAN link
SLIP (Serial Line Internet Protocol) is a legacy UNIX physical layer protocol for providing serial connections between two networks, or between a network and a remote node. Because of the universal nature of serial connection devices and interfaces, such as the RS-232 interface, SLIP was embraced.
PPP was designed to address the shortcomings of SLIP and the need for standard Internet encapsulation protocol. PPP (Point to Point Protocol) is the next generation of SLIP, but works at both the physical and the data link layers. PPP includes enhancements such as encryption, error control, security, dynamic IP addressing, multiple protocol support and automatic connection negotiation. PPP will work over serial lines, ISDN, and high-speed WAN links. The PPP data frame is shown in Figure 1-11.

Figure 11 PPP data frame
In addition to a frame with data, there are other frames that PPP uses. An LCP (Link Control Protocol) frame is used to establish and configure the connection.{Answer to Self Test Question #38} An NCP (Network Control Protocol) frame is used to select and configure the network layer protocols. Explicit LCP frames are used to close the link.
Frame Relay is a widely used packet-switched WAN protocol standardized by the ITU-T. Frame Relay relies on the physical and data link layer interface between DTE and DCE devices. Frame Relay networks are either public, and provided by carriers, or privately owned. Frame Relay is a widely used packet-switching WAN protocol standardized by the ITU-T. The key benefit of Frame Relay is the capability to connect with multiple WAN sites through a single link. This makes Frame Relay much cheaper than point-to-point circuits for large WANs. Dedicated point-to-point circuits connect the customer into a nearby Frame Relay switch at the carrier. From there, the Frame Relay switches work like routers, forwarding packets through the carrier's network, based on addressing in the packet header.
Frame Relay is very similar to the X.25 protocol. It uses a virtual circuit-permanent (PVC) or switched (SVC)-between the source and destination, and uses statistical multiplexing for managing multiple data streams. Because of the reliability of the media, error correction is handled at higher protocol layers. There is a CRC to detect and discard corrupted data, but Frame Relay does not request retransmission. Instead Frame Relay relies on higher-level protocols for error correction.
{Answer to Self Test Question #41}
SVCs are temporary links best used in networks with sporadic data transmission. An SVC session begins with a call setup that creates the virtual circuit. Then comes the data transfer, then an idle phase for a defined period, keeping the circuit open in case of more data. Finally, there is a call termination.PVCs are permanently established links and are the most common implementation of Frame Relay. There are only two session operations, data transfer and idle. The carrier service configures the PVC, since it is routed through the carrier's internetwork. (See Figure 1-12.)
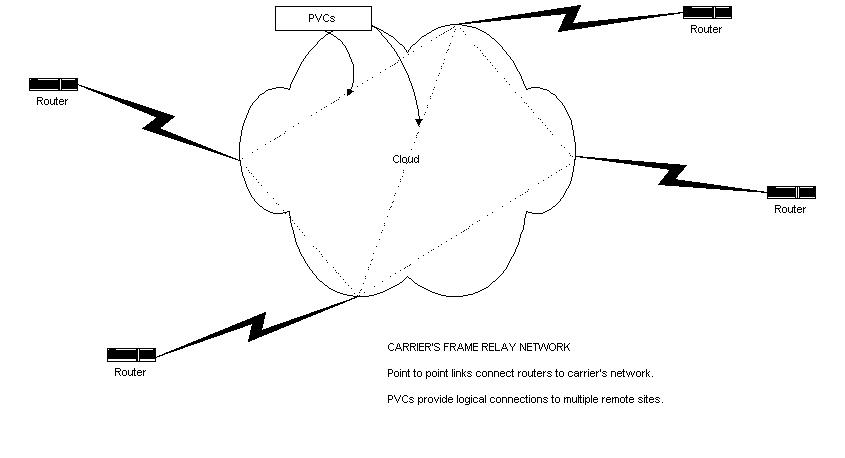
Figure 12: Carrier's Frame Relay Network
An important concept to know about Frame Relay is Data Link Connection Identifier (DLCI). The DLCI is a number used locally by a DTE and assigned by the Frame Relay provider.{Answer to Self Test Question #40} It refers to the connection between two DTEs in the Frame Relay network. Because it is a local identifier, each DTE may use a different number to identify the link.
Begin Q&A
|
Shari is configuring the DLCI for a PVC between Portland and Phoenix. The provider gave her two numbers: 12 and 14, and assigned them to the link. Shari arbitrarily uses 12 for Portland and 14 for Phoenix. When the link is completely configured, it does not work. Why? |
The provider should have specified that the DLCI for Portland was 14 and that the DLCI for Phoenix was 12. The local identifier was wrong and the link did not come up. |
In order to maximize throughput, flow control uses a congestion notification method.
{Answer to Self Test Question #39} FECN (forward-explicit congestion notification) is a bit in the frame that is set to a "1" when the frame experiences congestion between source and destination. The DTE device sends this information to upper protocol layers in order to begin controlling the flow. BECN (backward-explicit congestion notification) is a bit that is set to "1" when an FECN frame has been received that experienced congestion between source and destination. FECN and BECN are one-bit fields may be set to "0" as well, which means there is no congestion or that the congestion notification feature is not implemented by the switches in the network. The bits exist in the header at all times, no matter what their value. (See Figure 1-13)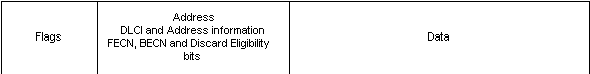
Figure 13 Frame Relay frame format
{Answer to Self Test Question #42}
The ITU-T X.25 standard describes the physical, and data link, and network layer protocols for a legacy packet-switching protocol. The physical layer protocol is X.21, which is roughly equivalent to the RS-232 serial interface. The data link layer protocol is LAPB (Link Access Protocol Balanced). The network layer specifies PLP (Packet Level Protocol).{Answer to Self Test Question #43}
Like Frame Relay, X.25 uses PVCs and SVCs, but its link speeds of 9.6 to 256 Kbps are slower. The data transfer rate is relatively slow compared to newer protocols, because X.25 was defined when media transmission quality was poor. As a result, the protocol specifies that each switching node must fully receive each packet and verify that there are no errors before sending it on to the next node. X.25 may utilize variable-sized packets. As a result of the hop-by-hop error checking and retransmission, and the variable packet size, X.25 is very slow. With the reliability of today's transmission lines, X.25 has a hard time competing with higher-performance protocols, like Frame Relay, that do not offer guaranteed delivery. Frame relay has no error recovery at all-errored packets are dropped without notification. Error checking is only done when the frame-relay frame gets to its final destination.X.25 uses a point-to-point connection between DTE and DCE. Via a PAD (packet assembler/disassembler), the DTE connects to a carrier-provided DCE, which in turn connects to a packet-switching exchange (PSE or switch), and eventually reaches a destination DTE.
Integrated Services Digital Network was standardized by the ITU-T. It was developed as a project to upgrade the Public Switched Telephone Network (PSTN) to a digital service. The physical specification for transmission medium is copper wire.
There are several components to ISDN, as illustrated in Figure 1-14. There is terminal equipment, network termination, and adapters of the following types.
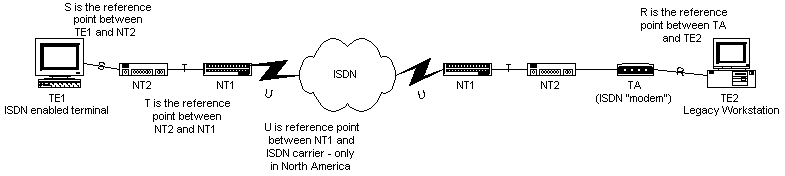
Figure 14 ISDN equipment connections
When ordering ISDN, consumers usually have the choice between BR (Basic Rate) and PR (Primary Rate) and Hybrid. There are various digital channels that make up these two configurations. The available digital channels are:
BR consists of two B channels and one D channel, and with control information has an effective bit rate of 192 Kbps. PR consists of one D channel and 23 B channels, with a bandwidth of 1.544 Mbps. In Europe, PR has one D channel and 30 B channels. Hybrid is a single A channel and a single C channel.
Note that LAPD (link access procedure for the D channel) is the signalling protocol used to set up ISDN calls for ISDN BRI at the data link layer.
{Answer to Self Test Question #44}
ATM (Asynchronous Transfer Mode) is a cell-switching protocol that uses a fixed 53-byte cell length and a cell relay method that reduces transmission delays. ATM can transmit voice, video, and data over variable-speed LAN and WAN links from DS-1 (1.544 Mbps) to as high as 622 Mbps. The key to ATM's high speed is within the fixed cell length. The fixed cell length enables routers to relay cells at the hardware level, using less processing power and increasing the data transmission.The ITU-T developed ATM as the result of a broadband integrated services signal network study. It evolved further from the work of the ATM Forum founded by Cisco, Net/Adaptive, Northern Telecom and Sprint. The technology used is VLSI (very large-scale integration), which segments data frames at high speeds into small, fixed units known as cells.
VLSI technology made possible the development of ASICs (application-specific integrated circuits) specifically to perform the segmentation and reassembly of data in hardware rather than in software. Along with the fixed cell size, this is what makes it possible to operate ATM circuits efficiently at such breathtaking speeds, now up to OC-48 (2 Gbps).
The cells relay through ATM switch devices that analyze the cell header and switch it to the correct output interface, in a switch-to-switch path until the cell reaches its final destination. The asynchronous method uses time slots that are available upon demand, rather than strict and wasteful time division multiplexing.
{Answer to Self Test Question #45}
There are two header formats: UNI and NNI (Network Node Interface). UNI is the communication between end nodes and ATM switches. NNI is the communication between two ATM switches. The diagram in Figure 1-15 displays the two different header formats.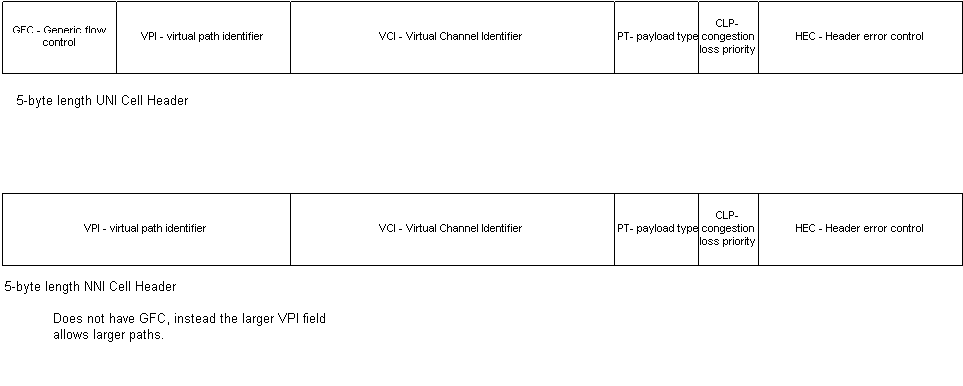
Figure 15 UNI and NNI cell header formats
ATM uses its own reference model, parts of which are analogous to the OSI reference model. The ATM layer and the ATM adaptation layer are roughly equivalent to the data link layer, and the ATM physical layer is analogous to the OSI physical layer.
The ATM physical layer is responsible for the bitstream transmission. The ATM physical layer contains two sublayers: physical medium and transmission convergence. The physical medium transmits the bitstream and timing synchronization information. The physical media that are supported are SONET/SDH, DS-1, DS-3/E3, OC-3, OC-12, 155 Mbps UTP, 100 Mbps FDDI, and 155 Mbps Fiber Channel. The transmission convergence manages cell delineation and header error control data, and packages ATM cells into frames that work with the physical media.
The ATM layer establishes connections and relays cells using the cell header information. It is responsible for mapping network layer addresses to ATM addresses. The ATM adaptation layer (AAL) translates the larger data packets into cells.
ATM is similar to Frame Relay in its switching mechanisms. Instead of switching variable-length packets over PVCs and SVCs, ATM switches fixed-length cells through the internetwork. ATM devices connect directly to an ATM switch.
In order to deliver voice, video, and data in an appropriate fashion, ATM has implemented new features. One of these is called Quality of Service (QoS). Quality of Service allows an ATM device to prioritize data based on the content. Thus, delivery of a file transfer can take a backseat to a video transmission, since the bursty data transfer of the file will not affect the quality of the service. On the other hand, a video transmission that stopped in the middle of a screen would be considered problematic.
Network Layer and Path Determination
The main services provided at the network layer are logical addressing of the node and network segments. As a result, the routing of data between the logical addresses is handled at the network layer. IP of the IP protocol suite is considered a network layer protocol. Data is broken into "packets" at this layer.
The network layer is where internetworking takes place. While the data link layer protocols have features that enable data to be passed from one node to another node on the same link, network layer protocols enable data to be passed from one network to another. This means that the network layer protocols must always contain addressing information that uniquely identifies networks within the internetwork.
Networking itself is the capability to share data between two nodes. Being able to simply locate the nodes on the network is one of the most basic and important functions in networking. The network layer not only provides a unique node address, but also a unique network address. This enables the routing of data between networks.
Layer 3, or the network layer, is where addressing is most important. When applying the OSI reference model to the IP protocol suite, IP (Internet Protocol) would be at layer 3. The IP addressing scheme determines the network that a node is on and the logical node address on the network. The logical node address is often the same as the MAC address in other protocols, although it is not in IP. This is dealt with on the lower data link layer (layer 2). Note that in Novell IPX, for instance, the MAC address is used for the network-layer node address without modification.
A network layer address is also called a logical address or software address.
{Answer to Self Test Question #17}Network layer addresses are hierarchical, and provide both the network and the node address. A router can easily separate the addresses to be sent on a particular interface by simply looking at the initial network portion of the address-the network address. When the packet reaches the destination network, the node address portion is used to locate the specific station.Routed Protocols vs. Routing Protocols
Routed protocols are used by end nodes to encapsulate data into packets along with network-layer addressing information so it can be relayed through the internetwork. AppleTalk, IP, and IPX are all routed protocols. When a protocol does not support a network layer address, then it is a non-routed protocol.
Routers use routing protocols to build and maintain routing tables and to forward data packets along the best path toward their destination networks. Routing protocols enable routers to learn about the status of networks that are not directly connected to them, and to communicate to other routers about the networks they are aware of. This communication is carried out on a continuing basis so the information in the routing table is updated as changes occur in the internetwork.
The characteristics that distinguish one routing protocol from another include:
Examples of routing protocols include RTMP, OSPF, and RIP.
Routing Algorithms and Metrics
A routing algorithm is the calculation that the routing protocol uses to determine the best route to a destination network. The simpler the routing algorithm, the less processing power the router will use. This, in turn, keeps the overhead low on the router.
Metrics are values used to determine which route is preferable. Depending on the routing protocol, different factors determine a route's metric, including the number of hops, link speeds, delay, reliability, and load. The resulting metrics are stored with the routes in a routing table or a link-state database.
Transport Layer
The transport layer provides data transport services, effectively shielding the upper layers from data transfer issues. Transport layer services are concerned with the reliability of the connection, establishing virtual circuits, error detection and recovery, and flow control. When the OSI model is applied to the IP protocol suite, TCP and UDP are both transport layer protocols.
{Answer to Self Test Question #18}
Transmission Control Protocol (TCP) is considered a reliable, connection-oriented protocol. User Datagram Protocol (UDP) is unreliable and connectionless. The difference between a reliable and unreliable protocol is the acknowledgment to the sender that data has been received. There is more overhead involved with a reliable protocol because of the acknowledgments. On the other hand, unreliable protocols do not guarantee delivery of data, and can be prone to more errors in delivery.Connectionless, or unreliable, protocols are used quite often when reliability issues such as sequencing and error recovery are addressed at the application layer. The advantage is that because they have fewer features, the overhead is very low.
Windowing
When some transport protocols negotiate a reliable connection between two nodes on an internetwork, they also negotiate a moving target of the amount of data that can be transmitted at any one time. That moving target is called a sliding window. This process is called Windowing.
Upper-Layer Protocols
The term upper-layer protocols refers to the session, presentation, and application layer protocols. The application layer provides basic services such as file transfer and network management to applications. It establishes the availability of destination nodes, and identifies the application synchronization between the nodes.
{Answer to Self Test Question #19}
Presentation layer is aptly named, for this layer handles the formatting of data, or presentation of that data. Services in the presentation layer include data encryption. The presentation layer protocol can also negotiate the syntax of the data in order for translation to occur with the destination node.As the name implies, the session layer establishes the session between two network nodes, maintains it, and terminates it as well. Services at this layer include class of service, data prioritization, and reporting errors for the upper two layers.
Cisco Routers, Switches, and Hubs
{Answer to Self Test Question #46}
Cisco IOS Software (Internetworking Operating System) is the software that runs on the Cisco products. This platform is integral to the interoperations of network devices in a Cisco internetwork. Cisco IOS includes security, access control, authentication, firewall, encryption, management services, and support for IBM connectivity, switching, voice and multimedia, and quality of service. The main purpose of IOS is to boot the Cisco hardware and begin the optimal transport of data across the internetwork.Of the internetwork routers available from Cisco, the Gigabit Switched 12000 series routers are built to handle the fastest backbone traffic. Gigabit switched traffic is standard, where the backbones of these routers can handle up to 4, 8 or 12 cards (depending on which router selected) that are OC-3 to OC-48 compliant. The target network for a Gigabit Switched 12000 series router running Cisco IOS are Internet service providers, enterprise WAN backbones, and other high-throughput internetworks needing speeds of even 2.4Gbps and up. It supports SONET, ATM, and DS-3/E-3 connections.
The platform for multiprotocol routers is the Cisco 7000 series routers, which run the Cisco IOS. The 7500 high-end series features Cisco Extended Bus (Cybus) which is connected to the external network through network interfaces connected to modular interface processors. The 7500 series supports any combination of the following.
In order to avoid network service interruption, the 7500 series supports online software reconfiguration without rebooting, online insertion and removal of new interface processors without rebooting, a fast boot process, self-diagnostics, and dual power supply options for some of the versions.
Cisco offers several routers built to provide the price and performance needed in smaller, workgroup-oriented LANs and WANs. These routers include the 2500 series, the 3600 series and the 4000 series. They support the most widely used protocols and physical media, from Ethernet and Token Ring to FDDI.
Switching services are becoming more popular due to the immediate speed improvements they can bring to a LAN. Switches can be connected to hubs or directly to workstations and servers. The algorithms used to determine the location of a hardware device effectively give each port a full throughput of 10 Mbps on Ethernet 10BaseT LANs. The Catalyst series switches normally come with a 100BaseT port, or ports, allowing the switch to be connected to a 100BaseT backbone or high-performance server. The most common Catalyst switch is the 2820, or 1900 version.
Catalyst 1900/2820 switch is a flexible switch that can be integrated in anything from a small LAN to an enterprise WAN.
{Answer to Self Test Question #47} It includes three switching modes: fastforward, fragmentfree, and store and forward. The fastforward mode begins forwarding a frame as soon as the MAC address is learned. Fragmentfree mode begins forwarding a frame as soon as it reaches 64 bytes, which is determined to be the threshold for fragment size. And store and forward receives the complete frame and checks it for errors before forwarding it. Fastforward is the default, as well as fastest mode. Store and forward is automatically used for packets travelling between 10 Mbps ports and 100 Mbps ports. The mode must be set for the switch if fastforward is not desired. The spanning tree protocol (IEEE 802.1d standard) is used for transparently reconfiguring the switch when the network topology changes.Hubs are also available from Cisco in the FastHub Series. FastHubs are Ethernet hubs that can be used alone, stacked together in a LAN workgroup, or connected to Catalyst Switches to form VLANs (Virtual Local Area Networks). Other Cisco products available include: Frame Relay PAD/routers, access routers for remote access users, ISDN routers, ATM switches, firewalls, and other network management hardware solutions.
Configuring a Cisco Switch and Hub
For any type of switch or hub, the following instructions apply.
There is a method to setting up a Cisco Catalyst 2820 switch.
{Answer to Self Test Question #20}This method demonstrates out-of-band management. That is, it manages the switch from a terminal that is directly connected to a serial port on the switch. This method has the advantage of working regardless of whether network connectivity is available from the switch. The steps to setting up a Cisco Catalyst 2820 switch are:Installing a FastHub 316C or FastHub 316T begins with the same unpacking and verification procedures as the switch installation. After unpacking and physically installing the hub, it can be further configured.
Certification Summary
A model for internetworks had to answer the challenges of interoperability and interconnectivity. These challenges prompted the development of a layered protocol model, both as a standardized model and one that was accepted due to its popular use. TCP/IP developed as a four-layer popular model. The seven-layer OSI reference model was developed and standardized by the ISO. The seven layers of the OSI model are application, presentation, session, transport, network, data link, and physical. Data travels through the protocol layers at the source by being broken into smaller data units and having header information added for each layer. When the data is reassembled and passed to the upper protocols at the destination, the header is discarded for each layer that the data has passed through. This allows independence of layers from each other. The header addition for each protocol layer is called encapsulation.
The physical layer is responsible for the bitstream of data, and its transmission. The data link layer consists of two sublayers: Logical Link Control and Media Access Control. The MAC sublayer handles hardware addressing-MAC addresses. The LLC sublayer handles control information in the frames, which are the data units at the data link layer.
The IEEE (Institute for Electrical and Electronics Engineers) created an 802 series of standards for physical and data link layer protocols. These included the standards for Ethernet (802.3) and for Token Ring (802.5), among others. ANSI (American National Standards Institute) created FDDI, a physical and data link layer standard that uses optical fiber media.
Ethernet, originally created by DIX (Digital/Intel/Xerox) is a CSMA/CD protocol allowing all nodes access to the network. If a collision occurs, the protocol has a method of sensing the collision and retransmitting the data. Ethernet can use thick or thin coax or unshielded twisted-pair copper wire. The rate of data transmission is usually 10 Mbps, however, 1Base5 is 1 Mbps. The most common form of Ethernet is 10BaseT, but 100BaseT is gaining in popularity.
Token Ring is a token-passing ring topology that is wired in a star fashion. IBM initially developed Token Ring. The physical medium used is generally shielded or unshielded twisted-pair copper wire. In this protocol, any station that has data to send must wait until a token frame is received. When the token is received, that station may send the data. The receiving station copies the data and changes a bit on the header, then forwards that data on to the original sending node. When the sending node receives the frame, it releases the token and checks the header to see if the data was received at its destination. With Token Ring, there are no collisions, so data is only retransmitted if a frame is damaged.
FDDI (Fiber Distributed Data Interface) is a dual ring token-passing protocol, similar to Token Ring, based on fiber-optic media. This has high-capacity speed for 100 Mbps. The dual ring topology uses a similar token-passing mechanism to Token Ring, but includes the capacity for fault management by creating a single ring. FDDI can be installed without using hubs, and it uses the secondary fiber ring to recover from failures in the primary ring.
There are several physical interfaces used for connecting nodes to a network. The most prevalent of interfaces is the RS-232 serial interface. V.35 is a physical layer protocol. HSSI is a high-speed serial interface suitable for WAN connections. BRI interfaces are used to connect to an ISDN line.
WAN links include Point to Point Protocol, which is a standard IP protocol used to encapsulate data over IP, and can be used over serial connections. Frame Relay is a packet network standard. X.25 is a legacy packet network standard that is very slow as a result of its error checking at each packet switch in the data path. ISDN connects to the digital telephone network. ATM is a cell-switching protocol for high-speed LAN and WANs.
The network layer defines logical addresses for network nodes. Routed protocols support network and node addressing at this layer, enabling packets to be routed through the network. Routing protocols determine the path between two networks by using routing algorithms and metrics, and by advertising their routes.
The transport layer handles reliability of data transfer, and can negotiate a sliding window of data transmission in order to maximize throughput on a network.
The upper layer protocols-application, presentation, and session-handle the data from the application, its format (such as encryption), and the session settings between the source and destination nodes.
Two-Minute Drill
![]()
What were the two challenges of creating a network model? (select two)
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
A, D. Interconnectivity and interoperability were the challenges of creating a networking model.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
C. ARPANET was created by the DARPA project
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
D. OSI stands for Open Systems Interconnection
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
C. The layers of the OSI reference model—application, presentation, session, transport, network, data link, and physical—can easily be remembered with the mnemonic device: All People Seem To Need Data Processing.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
B. The term for wrapping a data unit with a header is encapsulation.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
A. Hardware addresses are defined at the MAC portion of the data link layer.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
D. The IEEE (Institute of Electrical and Electronics Engineers) created the 802 standard series.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
B. DIX (Digital, Intel, and Xerox) co-created Ethernet.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
B. The function of CSMA/CD is to detect collisions. Nodes access the network. If they detect a collision, they retransmit the data.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
D. A backoff algorithm is used to prevent two nodes from retransmitting simultaneously and creating an endless number of collisions by delaying the retransmission for a variable length of time on each node.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
A. The two specifications are nearly identical, since 802.5 was based on IBM’s Token Ring specificiation.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
C. Beaconing is a Token Ring mechanism for notifying other stations that a serious error has occurred on the network.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
A, C. There is a token frame and a data frame used on a Token Ring network.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
C. FDDI specifies protocols at both the MAC sublayer and the physical layer of the OSI reference model.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
A. RS-232 is an extremely common serial port interface.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
D. The maximum data transmission rate for HSSI is 52 Mbps.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
C. A hierarchical network layer address provides the address of the network as well as the individual node.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
B. TCP is a connection-oriented, reliable transport layer protocol.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
B. The presentation layer of the OSI reference model is concerned with data formats and syntax.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
D. Out-of-band management is network fault tolerant, because it can manage a switch or hub even when network services are interrupted.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
B. Interoperability involves making sure that the data can be understood by equipment manufactured by different vendors that use different operating systems, hardware or languages.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
C. OSI is a de jure standard. De jure implies a standard accepted as legal by a certain organization-in this case, a standards body called International Organization for Standardization (ISO).
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
E. Use of a layered approach such as the one described by the OSI seven-layer model will result in reduced cost, and ultimately increases marketability of a product
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
B. At the source, each lower layer adds its own header information to the data it receives from the layer above it. At the destination, this process is reversed until the data is delivered to the application.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
D. Encapsulation in the OSI model occurs at all layers of the source.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
C. The session layer is usually implemented in the software. The physical and data link layers are usually implemented in hardware and software. The remaining layers are usually implemented in the software.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
C. bits. At the physical layer in the OSI model, the data is broken into smaller frames.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
C. Collision occurs only when nodes attempt to send the data simultaneously.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
B. In a broadcast system all the nodes see all data frames, whether or not that data is meant to be received by that node.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
F. The preamble is an indication of the start of a new frame. It contains alternating zeroes and ones.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
C. The FCS includes a CRC value.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
B. When a node receives the token, if the node has data to transmit, it flips a bit in the token and transmits the data. If the node has no data to transmit, it sends the token to the next node.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
C. When a node receives the token, if the node has data to transmit, it flips a bit in the token and transmits the data. If the node has no data to transmit, it sends the token to the next node.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
C. Dual ring architecture mainly provides fault tolerance. If a station on the dual ring fails (or if a break occurs in one of the rings), the dual ring is "wrapped" so that traffic doubles back the route it came from.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
C. The MAC address is network independent, such that wherever the hardware is plugged into the network, it would have the same MAC address.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
C. The BRI consists of two B channels at 64 Kbps and one D channel at 16 Kbps.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
C. Synchronization of network timing is done at the physical layer and involves an electrical signal generally provided by the carrier network.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
D. A Network Control Protocol frame in a Point to Point Protocol is used for selecting and configuring the network layer protocol. A Link Control Protocol (LCP) is used to establish and configure a connection.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
E. Both FECN and Backward Explicit Congestion (BECN) contain a bit that is set to "1" and is sent by DTE to upper protocol layers to notify of traffic congestion between source and destination.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
C. Data Link Connection Identifier in a Frame Relay network identifies a connection between two DTEs.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
A. PVC is a permanently established link. SVC terminates after the call has ended. Both SVC and PVC have a data transfer phase and an idle phase.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
F. The ITU X.25 Standard applies to the physical and data link layers' protocols.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
B. The data rate range for X.25 is from 9.6 Kbps to 256 Kbps.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
C. ATM is a cell-switching technology that can be used to transport data in a variety of different formats, including voice, video and bursty LAN data.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
D. The two header formats in ATM terminology are: User Network Interface (UNI) and Network Node Interface (NNI).
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
D. Cisco Routers use IOS for configuration and router operation.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
C. The three switching modes included in Catalyst 1900/2820 switches are: fastforward, fragmentfree, and store and forward.