GLOBAL KNOWLEDGE NETWORKä CERTIFICATION PRESS |
Chapter 11
Virtual Local Area Networking (VLAN)
Certification Objectives
*Broadcast Control
*Functional Workgroups
*Enhanced Security
*Configure ISL Trunking
*IEEE 802.1Q Trunking
*Troubleshooting VLANs
*From the Classroom
*A Tour of the Cisco IOS Documentation
*
![]()
Certification Objectives
Imagine you are sitting at your desk and the Chief Information Officer (CIO) startles you with the latest article in the trade magazines on network design. "I just read this great article about how VLANs provide flexibility, improve performance, and reduce management costs! How can we implement VLANs in our network?" the CIO asks. Suddenly, the CIO is gone, leaving you with the task of integrating VLANs into your existing network.
You’ve probably heard the term VLAN and wondered, what are they and how can I use them?
{Answer to Self Test Question #11}The term VLAN is short for virtual local-area network and is most commonly associated with switches. Using VLANs in your network design can help you solve business and technical needs, but they should be used with discretion. Creating too many VLANs in your network design can cause an administrative nightmare. If your organization is going to invest in a Layer 2 switch that supports VLANs, take advantage of the switching technology. Layer 2 switches provide wire-speed forwarding of frames, and do not incur the latency that traditional software-based routers do. If you are going to build a switched network, try to switch using Layer 2 as much as possible, and route using Layer 3 when necessary. There are many new products appearing in the networking market that provide Layer 3 routing of frames at Layer 2 speeds, but they are beyond the scope of this chapter.It is important to fully understand your business and technical requirements when deciding how to use VLANs.
{Answer to Self Test Question #12}Remember that each VLAN you create essentially creates a Layer 3 network that must be routed, so unless your traffic is purely workgroup-based, you will always need a routing function in your network. The rapid growth of e-mail, intranets, and the Internet led to the rapid growth of server farms. Server farms can contain shared file, application, and database servers, usually grouped in a dedicated VLAN or VLANs, and require users to communicate across VLAN boundaries using a router. As a reminder, try to keep your design as simple and flexible as possible. Start simple first, then implement a more complex design if requirements can’t be met with the existing design. Use VLANs to make your life easier, not more difficult.In this chapter, we will review the benefits of VLANs and their close ties to switching. The configurations we use are based on the Cisco Catalyst 5500 platform.
Switching and VLANs
The original switches did not provide the capability to create VLANs, since they were used simply to forward frames rapidly between devices.
{Answer to Self Test Question #13}The market for switches grew quickly when shared media hubs could not keep pace with the growing demand for increased bandwidth due to client-server applications providing a graphical user interface (GUI).The key difference between a switch and hub is how they handle frames. A hub receives frames on a port, then copies and transmits (repeats) the frame to all of its other ports. In this way, it is repeating the signal, basically extending the length of the network segment to all attached stations.
{Answer to Self Test Question #14}A hub repeats all frames to all ports except the port the frame was received on: {Answer to Self Test Question #15}unicast frames (destined for a particular MAC address), broadcast frames, (destined for all MAC addresses on the local segment), and multicast frames (destined for a subset of devices on the segment). This does not scale well for larger numbers of users, since each workstation and server attached to the hub must examine each frame to determine whether it is addressed to its Layer 2 MAC address. The larger the network, the greater the number of frames the network interface card (NIC) must process, wasting valuable CPU cycles. Hubs are cheaper than switches, and they are sufficient for small workgroups and transmissions that are short and bursty in nature.A frame switch handles frames intelligently—the switch reads the source MAC address of inbound frames and saves this information in its switching table. This table contains the MAC address and its associated port. {Answer to Self Test Question #16}The switch builds this table in volatile memory so it knows which MAC addresses are on each of its ports. The Catalyst switch learns these addresses by examining each frame as it is read into memory, adding new addresses to the switching table if not previously stored. In Cisco switches, this table is referred to as the CAM (content-addressable memory) table. This table is constantly updated and rebuilt every time the switch is powered on, and you can adjust the refresh timers higher or lower depending on your needs. Figure 11-1 shows the CAM table from a Catalyst 5000.
In this example, the VLAN column refers to the VLAN number the destination port belongs to. The Destination MAC column refers to the MAC address learned from the port. Remember that multiple MAC addresses can be associated with the same port, so verify the number of MAC addresses your switch can support. The Destination Ports column describes which port the MAC address was learned from.
Cat5500> show cam dynamic
VLAN Destination MAC Destination Ports or VCs
---- ------------------ ------------------------
1 00-60-2f-9d-a9-00 3/1
1 00-b0-2f-9d-b1-00 3/5
1 00-60-2f-86-ad-00 5/12
1 00-c0-0c-0a-bd-4b 4/10
Cat5500>
Figure 1 Cisco CAM table
Next, the switch examines the destination MAC address of outbound frames and immediately looks in the switching table. If the switch finds the matching address, it copies the frame only to that port. {Answer to Self Test Question #17}If it does not find the address, it copies the frame to all ports. Unicast frames are sent only to the necessary port, while multicast and broadcast frames are repeated to all ports.
Switching was introduced as a "new" technology that increased bandwidth and improved performance, but essentially, switches are high-density bridges with additional features. {Answer to Self Test Question #18}Switching is a term most commonly used to describe Layer 2 network devices that forward Ethernet and Token Ring frames based on the destination Media Access Control (MAC) address.
The two most common methods vendors use to forward traffic through switches are cut-through and store and forward.
Cut-through switches generally achieve lower port-to-port latency than store-and-forward because in this mode, the switch can begin forwarding a frame to its intended port without waiting until is has received the complete incoming frame. The switch only has to read enough of the frame to identify the source and destination MAC addresses located near the beginning of Token Ring and Ethernet frames. Most cut-through switches start forwarding once the first 30 to 40 bytes of the frame header have been received.
{Answer to Self Test Question #19}
Store and forward switches receive the entire frame before it is switched. This method incurs more latency but has more advantages. The capability to filter and manage and control traffic is a major benefit of this approach. In addition, runts and damaged frames are not propagated, since they are not valid frames. {Answer to Self Test Question #20}Switches must have memory buffers to read in and store the frames before making their switching decision, which increases the cost of the switch.As switching technology improved and the market embraced switching as the new craze, VLANs began to appear. The easiest way to understand Virtual LANs is to compare them to physical LANs. A physical LAN can be a group of end stations, bounded by a router or routers, which share a common physical connection.
{Answer to Self Test Question #21}A VLAN is a logical collection of end stations on the same Layer 2 (and Layer 3) segment, which communicate directly without a router. Traditionally, users in separate physical locations would need to communicate to other’s segments using a router. Switches with VLAN capabilities were initially implemented in the core of large campus networks, and for smaller workgroup networks. Initially, switching was deployed as needed, but it is now common to implement switching and VLANs to the desktop.{Answer to Self Test Question #22}
Each end station on a VLAN (and only those end stations) process broadcast traffic sent by other VLAN members. For example, workstations A, B, and C are connected to VLAN 1. VLAN 1 contains three Catalyst 5500 switches. Each switch is located on a different floor and connected via fiber, communicating via a trunking protocol. Workstation A is connected to switch A, workstation B is connected to switch B and workstation C is connected to switch C. If workstation A sends a broadcast frame, workstations B and C will receive the message, even though they are physically connected to different switches. Workstation D is connected to switch A, but defined to VLAN 2. When D sends a broadcast, workstation A does not see the traffic, because even though they are on the same physical switch, they are not in the same virtual LAN, and the switch will not forward the traffic to A. Remember that VLANs operate at Layer 2, so communication among VLANs requires a Layer 3 routing decision. In addition, workstations B and C do not see broadcasts from D. {Answer to Self Test Question #2}Virtual LANs (VLANs) offer the following primary benefits:
{Answer to Self Test Question #6}Unlike traditional LANs bounded by a router/bridge interface, a VLAN can be viewed as a broadcast domain with logically configured boundaries. VLANs offer more freedom than traditional LANs.
{Answer to Self Test Question #23}Previous designs were based on the physical limitations of hub-based networks; basically, the physical boundaries of a LAN segment were limited to the effective distance an electrical signal could travel from a hub port. Extending LAN segments beyond these effective distances required the use of a repeater, a device that strengthens and re-sends the signal. VLANs permit broadcast domains that are independent of physical location, the LAN media, the MAC type, and the transmission rates. Members can be located wherever they need to be rather than being forced to move to a specific location to connect to the LAN. VLANs increase network performance by containing broadcasts to a smaller and more manageable logical broadcast domain. In traditional switched environments that don’t support VLANs, all broadcast packets go to each and every individual port. Using VLANs, all broadcasts are confined to a specific broadcast domain.{Answer to Self Test Question #24}
The most fundamental benefit of VLAN technology is the capability to create workgroups based on function rather than on physical location or media. Traditionally, network administrators grouped users under the same functional department by physically moving users, their desktop and servers into a common environment such as a shared LAN segment. All team members had to be physically connected to the same media to take advantage of the localized higher-speed server connection. VLANs allow administrators to create, group, and regroup LAN segments logically and instantaneously, without changing physical infrastructure and taking users and servers down. The ability to easily add, move, and change users to the network is a key benefit of VLANs.VLANs also offer the added benefit of security. Users in a defined group are prevented from accessing another group’s data, because each VLAN is a closed, logically defined group. Imagine a company in which the Accounting department, working on confidential financial statements, is spread across all three floors of a building. The Engineering and Marketing departments are spread across all three floors as well. Using VLANs, the Engineering and Marketing workgroups can be located on all three floors as members of two different VLANs, and the Accounting department can be members of a third VLAN that spans all three floors. Now the network traffic generated by Accounting will only be accessible to employees of that department, and the Engineering and Marketing teams will not be able to access Accounting’s confidential data. Obviously, there are several other requirements to ensure complete security, but VLANs can be part of an overall network security strategy. Figure 11-2 illustrates how functional VLANs can span traditional physical boundaries.
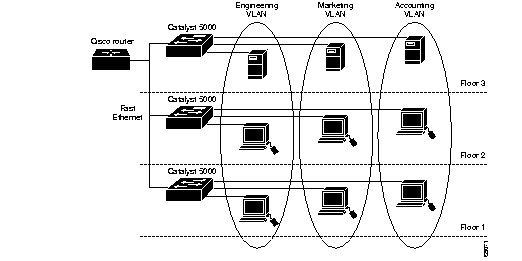
Figure 2 VLANs crossing physical boundaries
Since VLANs are defined within the device, they can be quickly and easily modified at any time to add, delete, move, or change users as required.
VLAN’s can be assigned by {Answer to Self Test Question #7}:
Port-based VLANs allow the assignment of switch ports to VLANs. Ports can be assigned individually, by groups, by entire row, and even across switches communicating via a trunking protocol. This is the simplest and most common method of VLAN assignment. It is common to implement port-based VLANs when assigning TCP/IP addresses to workstations using Dynamic Host Configuration Protocol (DHCP).
MAC address-based VLANs allow the user to participate in the same VLAN, even when the user moves from one location to another. This method requires the administrator to identify each workstation’s MAC address and then configure this information into the switch. This method can be complex to troubleshoot if a user changes MAC addresses. Changes to any desktop require communication to the network administrator, which can be an administrative burden.
Network address-based VLANs allow the user to participate in the same VLAN, even when the user moves from one location to another. This method moves the VLAN associated with the workstation’s Layer 3 address to each switch the user is connected to. This method can be useful in situations where security is important, and access is controlled to resources via access lists on routers. Thus, a user in the "secure" VLAN, can move to another building and still communicate to the same devices, because the Layer 3 address remains the same. Network address-based VLANs can be complex to troubleshoot.
Spanning-Tree Protocol and VLANs
The Spanning-Tree Protocol allows redundant physical links in bridged networks, yet only one physical link forwards frames. The protocol places redundant physical connections to the same network segment in blocking mode. When there is a change in the topology to these links, the Spanning-Tree Protocol re-calculates which link will forward frames, and blocks the rest. There are two major methods of bridging, transparent and source-route. {Answer to Self Test Question #26}Spanning-Tree Protocol is used in transparent bridging environments to ensure a loop-free path to every network segment participating in the calculation, while also provide redundancy in the event of failure.
{Answer to Self Test Question #27}
Transparent bridging is used primarily in Ethernet environments. It places the burden of determining the path from the source to the destination device on the bridges. Ethernet frames do not contain a Routing Information Field (RIF) like Token Ring frames, so devices simply send frames and assume that they will reach their destination. The process a bridge uses to forward frames is similar to the way Layer 2 switches operate. A transparent bridge examines the incoming frame and learns the destination MAC address. The bridge looks for this address in its bridging table; if it finds a match, it forwards the address out the corresponding port. If the MAC address is not found, it copies and forwards the frame out all connected ports except the port from which it came.{Answer to Self Test Question #25}
Source-route bridging is used in Token Ring environments. It places the responsibility of locating the destination device on the sending station. Token Ring devices send out a test frame to determine if the device is on the local ring. If no answer is received to the test frame, the device sends an explorer frame in the form of a broadcast. The broadcast is forwarded across the network by other bridges, with each bridge adding the ring number and bridge number it’s connected to, until the frame reaches its final destination. {Answer to Self Test Question #28},{Answer to Self Test Question #29}The combination of ring and bridge numbers is contained in the RIF field. The destination device responds to the explorer frame, and the source device eventually receives the response frame. Communication now begins with each station using the RIF value appended to each frame. Source-route bridges forward frames based on this RIF and do not build a bridging table of MAC addresses and ports, since the end devices provide the source-to-destination information in the RIF.{Answer to Self Test Question #30}
For our discussion, we will examine the problems associated with loops and transparent bridging, since they are most prevalent today. Imagine two network segments, segment A and segment B with one workstation on each: workstation A and workstation B, respectively. Two transparent bridges are connected to both segment A and segment B, creating a loop in the network. Workstation A sends a broadcast frame for workstation B, and both bridges read the frame from their segment A interfaces and forward it out their segment B interfaces. Both bridges associate the address of workstation A with their segment A interfaces in their bridging table. The Ethernet frame shows the source address as workstation A and the destination address as a broadcast. After the bridges forward the frames to segment B, the frame still contains the same source and destination address, since bridges operate at Layer 2 and do not change the source address when forwarding frames. The frame is received by both bridges on their segment B interfaces, and the bridges correctly forward the broadcast frame back to segment A, since bridges forward broadcasts out all other ports. In addition, the bridges update their tables to associate the address of workstation A with their segment B interfaces. The bridges will continue to forward these broadcast frames over and over. This obviously will degrade performance on the network, since every device will have to process the frame over and over, wasting each device’s CPU time, and consuming network bandwidth. This topology is illustrated in Figure 11-3.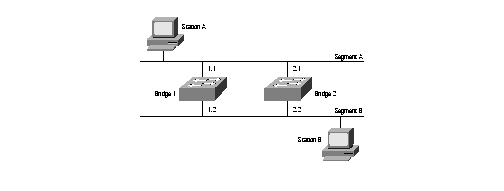
Figure 3 Redundant topology with loops
This is major reason the Spanning-Tree Protocol was developed—to eliminate loops in the network. {Answer to Self Test Question #5}The Spanning-Tree Protocol ensures this loop-free path by placing one of the bridge ports in "blocking mode", preventing the forwarding of packets. Note that the interface could be enabled in the event an active port in the network goes down. {Answer to Self Test Question #31}When there is a change in the topology of the network, the bridges re-calcuate the spanning tree by sending out Bridge Protocol Data Units (BPDUs). BPDUs are exchanged between devices in a transparent bridging environment to determine which ports need to be placed in blocking mode.
Now that we understand the basics of spanning tree, how do they pertain to switches? Switches function identically to bridges, so each switch participates in the spanning-tree process unless it is disabled. You should use extreme caution if you choose to disable spanning tree on your switch, since it can cause serious problems. Switches ensure a loop-free topology by executing the spanning-tree algorithm (STA). The spanning-tree algorithm will enforce a loop-free topology for each VLAN configured on your switch. Thus, connecting any network devices other than servers and workstations could cause a loop in your network if the spanning-tree process is disabled. The major problem created by loops in the network is a broadcast storm. This network state is created when switches or bridges continue to forward broadcast frames out each port they are connected to; other switches and bridges connected to the same networks creating a loop will continue to forward the same broadcast frames back to the forwarding switch or bridge. This problem severely degrades network performance, since the network devices are constantly busy copying the broadcast frames to all of their other ports.
Default VLAN Configuration
The Catalyst switch has several VLANs defined by default. VLAN 1 is defined, and all active ports are grouped in this VLAN. If you want to add more VLANs, you will need to create them using the SET VLAN command. VLAN 1 will appear using the name DEFAULT in any SHOW VLAN commands. {Answer to Self Test Question #32} In addition, VLANs 1002 – 1005 for FDDI and Token Ring are defined. You do not need to worry about removing these VLANs, since they are part of the default configuration. An example of the default configuration appears in Figure 11-4.
Cat5500> (enable) show vlan
VLAN Name Status Mod/Ports, Vlans
----------------------------------------------------------------
1 default active 1/1-2
3/1-24
4/1-24
1002 fddi-default active
1003 token-ring-default active
1004 fddinet-default active
1005 trnet-default active
VLAN Type SAID MTU Parent RingNo BrdgNo Stp BrdgMode Trans1 Trans2
---------------------------------------------------------------------
1 enet 100001 1500 - - - - - 0 0
1002 fddi 101002 1500 - 0x0 - - - 0 0
1003 trcrf 101003 1500 0 0x0 - - - 0 0
1004 fdnet 101004 1500 - - 0x0 - 0 0
1005 trbrf 101005 1500 - - 0x0 - 0 0
VLAN AREHops STEHops Backup CRF
---- ------- ------- ----------
1003 7 7 off
Cat5500> (enable)
Figure 4 Showing VLANs on a Catalyst 5500
Configuring a VLAN across a Domain
Any solid network design includes gathering the user requirements to determine the most efficient, simple, and logical use of network resources. Before creating VLANs on your switches, you should spend time creating a logical design of your network. Useful questions to ask include:
In order to exchange VLAN information between switches in your network, you will need to create trunk ports on your switches. A trunk port is any port or group of ports used to send VLAN information to other network devices connected and running a trunking protocol. A trunking protocol is the "language" that switches use to exchange VLAN information. Examples of trunking protocols include ISL and IEEE 802.1Q. Note that regular switch ports do not advertise VLAN information, but any ports can be configured to trunk VLAN information. You must activate trunking on the desired ports, as it is disabled by default. Trunk ports are ports dedicated solely to sending this VLAN information by a trunking protocol. Cisco switches commonly use the Inter-Switch Link (ISL) trunking protocol to provide the capability to communicate this information.
In order to automatically exchange VLAN information across trunk ports, you will need to configure Cisco’s VLAN Trunk Protocol (VTP), which allows switches to send VLAN information in the form of advertisements to neighboring devices. The information transmitted includes the domain, the revision number, active VLANs, and other information. You will configure servers and optionally, clients. The advantage of using VTP is that you can control the adding, deleting, or changing of VLANs in your switch design. The disadvantage is unnecessary traffic sent over trunk ports to devices that may not need that information. Cisco switches provide the capability to limit the VLAN information sent across trunk ports using the pruning option. {Answer to Self Test Question #8}Using VTP, you can ensure that any changes to your VLAN design are propagated to all switches running VTP in the same domain. VTP sends VLAN information via trunk ports to a multicast address, but not over regular switch (non-trunk) ports.
The other option is to configure the switch for transparent mode, and manually configure each VLAN on every switch that will contain devices participating in that VLAN. {Answer to Self Test Question #3}This is an important decision in your network design. If your network will contain many switches, containing many VLANs spanning across multiple switches, VTP probably makes sense. If your network design will remain fairly static, and VLANs will not be added or changed from the initial design, transparent mode may work better. VTP is required to use Cisco’s network management software, VLAN Director, to manage your switches. If administrative control is a concern, VTP can provide the solution. You have the option of setting a password on the VTP domain to control the changing of VLAN information in your network. In addition, by leaving the VTP server default option active on your core switches, you can control the update process. After configuring your VTP server switches, the rest of the switches in your network can be configured as clients, which can only receive VLAN information.
Exercise 11-1 Configuring VTP{Answer to Self Test Question #33}
{Answer to Self Test Question #34}
Verify that you have configured VTP by using the SHOW VTP STATISTICS command, shown in Figure 11-5.Cat5500> (enable) show vtp statistics
VTP statistics:
summary advts received 0
subset advts received 0
request advts received 0
summary advts transmitted 3457
subset advts transmitted 13
request advts transmitted 0
No of config revision errors 0
No of config digest errors 0
VTP pruning statistics:
Trunk Join Trasmitted Join Received Summary advts received from
non-pruning-capable device
-------- --------------- ------------- ---------------------------
1/1-2 0 0 0
Cat5500> (enable)
Figure 5 Showing VTP statistics on a Catalyst 5500
The output from the SHOW VTP DOMAIN command is shown in Figure 11-6. The Domain Name value is the name provided when you use the SET VTP DOMAIN <name> command. The local mode specifies server, client, or transparent mode. Servers can update VLAN information in a VTP domain; clients only receive VLAN information. The Vlan-Count field identifies the number of VLANs configured on this switch.
Cat5500> (enable) show vtp domain
Domain Name Domain Index VTP Version Local Mode Password
-------------------------------- ------------ ----------- ----------- ----------
Cisco 1 2 server -
Vlan-count Max-vlan-storage Config Revision Notifications
---------- ---------------- --------------- -------------
6 1023 4 disabled
Last Updated V2 Mode Pruning PruneEligible on Vlans
--------------- -------- -------- -------------------------
172.16.21.252 disabled disabled 2-1000
Cat5500> (enable)
Figure 6 Showing VTP configuration on a Catalyst 5500
Another option when configuring VLANs is to use a friendly name when adding VLANs to your network. In practice, it’s simpler to use numbers, and document that information on your switches. It may be easier for your users to refer to VLAN 1 as the Marketing VLAN, or refer to VLAN 2 as the Sales VLAN. If your organization decides to invest in Cisco’s Route Switch Module (RSM), you will probably want to stick with the numbering scheme for your VLANs. The RSM is basically a full-feature Cisco router that resides in Catalyst 5x00 series switches. The RSM does not have any external interface ports, because it contains an interface to the backplane of the Catalyst switch. Interfaces are configured as VLANs on the RSM, and correlate exactly to the VLANs defined on your Catalyst switches. For administrative purposes, it’s easier to refer to numbers, so if users have issues on VLAN 2, you will easily remember which router interface to check when troubleshooting. If you decide to use friendly names for your VLANs, however, the Catalyst switch will support them.
Exercise 11-2 Configuring a VLAN with Names
If you want to name your VLAN, be sure to include the NAME parameter and the VLAN name in step 8.
Grouping Switch Ports to VLANs
The next step is to assign ports to your VLAN. This option provides the flexibility to efficiently assign switch ports to the necessary VLAN, without wasting ports. Let’s say you have a Catalyst 5500 with ten 24-port cards, for a total of 240 ports. Now, let’s assume you have 60 users in VLAN 1 and you expect they will grow to 150. You also have 40 users in VLAN 2 and expect them to grow to 80. You could define exactly 60 ports to VLAN 1 and 40 ports to VLAN 2, or you can assign the extra ports to support their expected growth.
In practice, it’s probably easier to define the additional ports for each VLAN and group them by physical card, to minimize the administrative burden. For example, assign your ports to VLAN 1 sequentially from card 3, port 1 through card 3, port 24. Repeat the assignment of VLAN 1 for cards 4, 5, 6, 7, and 8 to give you a total of 144 ports in VLAN 1. Now assign card 9, port 1 through card 9, port 24. Repeat for cards 10, 11 and 12 to give you a total of 96 ports in VLAN 2. Figure 11-7 illustrates the two VLANs and their associated ports.
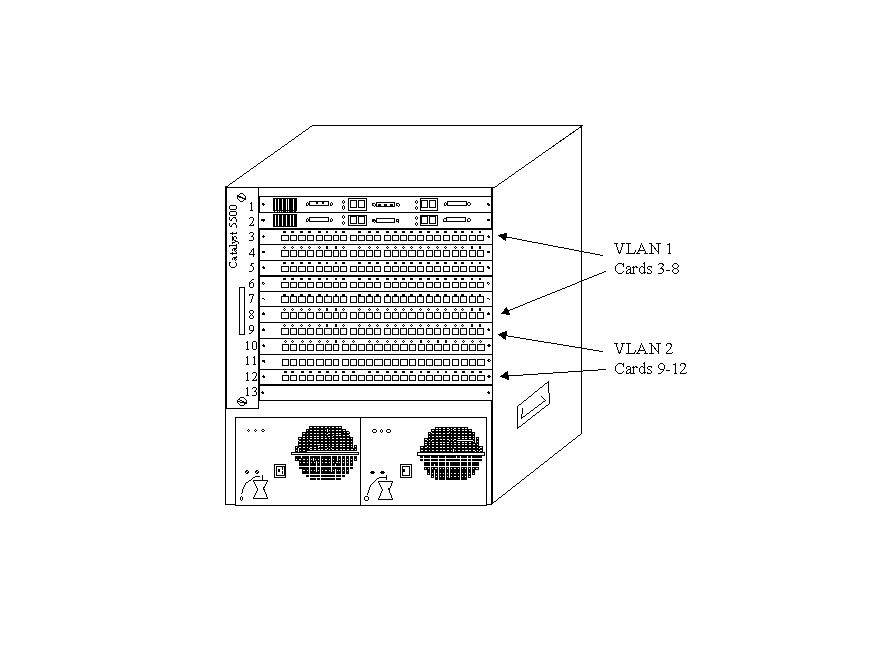
Figure 7 VLAN assignments
The assignment of ports to sequential cards will keep the cost of day-to-day user administration lower. Which is easier to understand—two VLANs assigned sequentially across a switch, or mixed between cards? For example, it would seem confusing if VLAN 1 was assigned to cards 3 – 6 and VLAN 2 is assigned to cards 7 – 8. Then VLAN 1 adds 24 more users to card 9. Now the importance of your network documentation just became greater. What if you are out sick and a relatively inexperienced person tries to add more users to VLAN 2, but plugs them into a card using VLAN 1? Remember to keep it simple.
It’s important to note the different options available for grouping switch ports based on the type of line card module. The Catalyst 5000 24 Port 10/100 Dedicated Switch Module lets you configure each port to be in a separate VLAN, if needed. The Catalyst 5000 24 Port 100 Mb Group Switching Module contains three switch ports across the 24 user ports. Ports 1 – 8 are tied to switch port #1, Ports 9 – 16 are tied to switch port #2, and Ports 17 – 24 are tied to switch port #3. Thus, you could define a maximum of three different VLANs on the group-switching module. Reserve time to read the configuration guide included with your hardware to understand which VLAN grouping features your card supports.
For our configuration example, we will configure a 24 Port 10/100 Dedicated Switch Module. You should have already configured your VLAN from Exercise 11-2, but it is not required. In the next exercise, there are ten line cards in slots 3 – 12, and VLANs 1 and 2 have already been defined. {Answer to Self Test Question #35}Remember that you are free to assign ports in the manner best for your organization—assigning them sequentially is only a suggestion to simplify administration.
Exercise 11-3 Grouping Switch Ports to VLANs {Answer to Self Test Question #36}
Verify that you have configured your switch ports correctly using the commands in Figures 11-8 and 11-9.
Cat5500> (enable) show port status
Port Name Status Vlan Level Duplex Speed Type
----- ------------ ---------- ---------- ------ ------ ----- ------------
1/1 SUP II PRIMARY connected trunk normal full 100 100BaseFX
1/2 SUP II PRIMARY connected trunk normal full 100 100BaseFX
3/1 connected 1 normal a-half a-100 10/100BaseTX
3/2 connected 1 normal a-full a-100 10/100BaseTX
3/3 connected 1 normal a-full a-100 10/100BaseTX
3/4 connected 1 normal a-full a-100 10/100BaseTX
3/5 notconnect 1 normal auto auto 10/100BaseTX
3/6 notconnect 1 normal auto auto 10/100BaseTX
3/7 notconnect 1 normal auto auto 10/100BaseTX
3/8 notconnect 1 normal auto auto 10/100BaseTX
3/9 notconnect 1 normal auto auto 10/100BaseTX
3/10 notconnect 1 normal auto auto 10/100BaseTX
Cat5500> (enable)
Figure 8 Showing port status on a Catalyst 5500
Cat5500> (enable) show vlan
VLAN Name Status Mod/Ports, Vlans
---- -------------------------------- --------- --------------------------
1 default active 1/1-2
3/1-24
4/1-24
5/1-24
2 VLAN0002 active 6/1-14
7/1-24
1002 fddi-default active
1003 token-ring-default active
1004 fddinet-default active
1005 trnet-default active
VLAN Type SAID MTU Parent RingNo BrdgNo Stp BrdgMode Trans1 Trans
---- ----- ---------- ----- ------ ------ ------ ---- -------- ------ -----
1 enet 100001 1500 - - - - - 0 0
2 enet 100002 1500 - - - - - 0 0
Cat5500> (enable)
NOTE: VLAN 1 is named "default" VLAN on Cisco switches
Figure 9 Showing VLAN assignments on a Catalyst 5500
After configuring your switch ports to VLANs, you should consider enabling the portfast option on your switch ports to reduce the chance for day-to-day connectivity problems. Remember that switches participate in the spanning-tree process; each switch port must ensure that its connection does not create a loop in the network. For example, imagine that a user accidentally plugs a crossover cable into a switch port on VLAN 1 and connects the other end to another switch port on VLAN 1. A loop has been created in the network, which must be eliminated. STA will take care of this, and during this process, both ports will progress through various stages during the calculation.
{Answer to Self Test Question #37}There are five major states a switch port can exist in:When a device is first connected to a switch port, the port goes from the blocking to the listening and learning states before it starts forwarding frames, assuming the spanning-tree process does not identify a redundant path.
{Answer to Self Test Question #9}Figure 11-10 illustrates these stages and potential paths.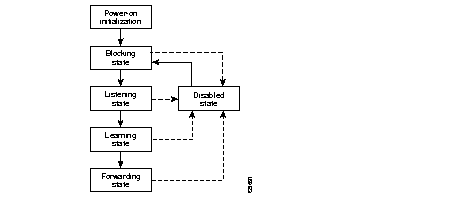
Figure 10 Port states
Fortunately, Cisco provides the capability to bypass this process when a device connects to the switch. {Answer to Self Test Question #38}The portfast option will place the port in the forwarding state, and bypass the listening and learning states.{Answer to Self Test Question #39}By default, portfast is disabled on all ports. A workstation or server that connects to a port with portfast disabled may initially behave as if it is not connected to the network. After the port changes to the forwarding state (after some period of time) the device will function normally. When portfast is disabled, workstations or servers may not be able to ping, acquire a DHCP address consistently, or log into a Novell Directory Services tree or NetWare server. The devices behave this way because the switch port is not forwarding these frames for the ping, DHCP request, and NDS login. You can avoid this problem by enabling the portfast option across all ports that you know will be used for workstations and servers. Use this command with caution, as it can cause loops in your network.
Exercise 11-4 Enabling Portfast
Cat5500> (enable) set spantree portfast 3/1-24 enable
Warning: Spantree port fast start should only be enabled on ports connected
to a single host. Connecting hubs, concentrators, switches, bridges, etc. to
a fast start port can cause temporary spanning tree loops. Use with caution.
Spantree port 3/1-24 fast start enabled.
Cat5500> (enable)
Figure 11 Enabling Portfast on a Catalyst 5500
Verify that you have configured portfast correctly using Figure 11-12. The Fast-Start column will either contain the value Enabled or Disabled. Enabled signifies that fast-start is enabled and the port will forward frames as soon as a device is connected and powered on. The number signifies the card number in the switch. You can also type the same command with no number to see the portfast information for all ports.
Cat5500> (enable) show port span 3
Port Vlan Port-State Cost Priority Fast-Start Group Method
-------- ---- ------------- ----- -------- ---------- ------------
3/1 1 not-connected 100 32 enabled
3/2 1 not-connected 100 32 enabled
3/3 1 not-connected 100 32 enabled
3/4 1 not-connected 100 32 enabled
3/5 1 not-connected 100 32 enabled
Cat5500> (enable)
Figure 12 Verifying portfast on a Catalyst 5500
(5)Configuring VLAN Trunks
Trunks are used to exchange VLAN information between switches, providing the capability to build VLANs that span physical boundaries. The concept of trunking is similar to routing protocols used by routers to build a network topology. Switches use trunking protocols used to determine which port to send frames if a VLAN spans physical boundaries. By using trunking protocols, the same VLAN can be defined on each switch located on each floor of a 12-story building. Catalyst switches support several different trunking methods:{Answer to Self Test Question #4}
It’s always a good idea to review the release notes for new versions of switch code, since they are adding new features and functionality. This helps ensure that your switch will support the features you need to successfully implement your network design.
Next, we will briefly discuss the ISL and IEEE 802.1Q trunking protocols and learn the commands to configure ISL. The IEEE 802.10 and LAN Emulation trunking methods are beyond the scope of this chapter.
ISL is a trunking protocol developed by Cisco exclusively for their products. It allows trunking between switches, and transports Ethernet, FDDI, or Token Ring frames between switches. Cisco routers running ISL can understand and route between VLANs without requiring a physical router interface port for each VLAN.
{Answer to Self Test Question #1}Using ISL, one Fast Ethernet router port can route between two VLANs on a switch.Exercise 11-5 Configuring ISL
Verify that you have configured your trunk ports correctly using the commands in Figure 11-13.
Cat5500> (enable) show trunk
Port Mode Encapsulation Status Native vlan
-------- ----------- ------------- ------------ -----------
1/1 auto isl trunking 1
Port Vlans allowed on trunk
-------- ---------------------------------------------------------------------
1/1 1-1005
Port Vlans allowed and active in management domain
-------- ---------------------------------------------------------------------
1/1 1,4-5,1003,1005
Port Vlans in spanning tree forwarding state and not pruned
-------- ---------------------------------------------------------------------
1/1 1005
Cat5500> (enable)
Figure 13 Verifying trunking on a Catalyst 5500
IEEE 802.10Q is an industry-standard trunking protocol developed for inter-operability. It allows the exchange of VLAN information between network devices of different manufacturers. For example, a Cisco switch running IEEE 802.1Q can communicate with another vendor’s switch running IEEE 802.1Q. The IEEE 802.1Q feature is available on the Catalyst series using switch code 4.1 and later.
{Answer to Self Test Question #10}Please reference the configuration guides for the configuration commands.Implementing VLANs requires additional tools to identify and resolve connectivity issues. There are several techniques to quickly identify and resolve connectivity problems using Catalyst switches. The following three problems and suggested solutions should help to reinforce the material we have covered in this chapter.
PROBLEM: A workstation on VLAN 1 can’t communicate with another workstation on VLAN 1. The workstations are connected to the same switch.
Suggestion #1: Check the port speed and duplex of the workstation in question. Cisco switches provide the auto-negotiate feature for speed and duplex of switch ports. Depending on the network interface card and software drivers, you can experience connectivity problems. In practice, it is very common to manually set the port speed and duplex.
Example: Use the command set port speed 3/1 10 to set the speed to 10 Mbps, as shown in Figure 11-14.
Cat5500> (enable) set port speed 3/1 10
Port 3/1 speed set to 10Mbps.
Cat5500> (enable)
Figure 14 Setting port speed on a Catalyst 5500
Use the command set port duplex 3/1 half to set the duplex to half, as shown in Figure 11-15.
Cat5500> (enable) set port duplex 3/1 half
Port 3/1 set to half-duplex.
Cat5500> (enable)
Figure 15 Setting port duplex on a Catalyst 5500
Use the command show port status 3/1 to verify the changes, as shown in Figure 11-6.
Cat5500> (enable) show port status 3/1
Port Name Status Vlan Level Duplex Speed Type
----- ------------------ ---------- ---------- ------ ------ ----- ------------
3/1 connected 1 normal half 10 10/100BaseTX
Cat5500> (enable)
Figure 16 Verifying port speed and duplex on a Catalyst 5500
Suggestion #2:
Check the VLAN assignment of the ports in question. Remember that devices connected to switch ports in different VLANs will not be able to communicate without traversing a router.PROBLEM: A workstation on VLAN 1 can’t communicate with another workstation on VLAN 1. The workstations are connected to different switches.
Suggestion #1: Check the VLAN assignment of the ports in question. Remember that devices connected to switch ports in different VLANs will not be able to communicate.
Example: Use the command show port mod_num/port_num to verify the VLAN assignment. Repeat this step on both switches for the correct port numbers. Verify that the workstations are connected and are members of VLAN 1, as shown in Figure 11-17.
Cat5500> (enable) sh port 5/1
Port Name Status Vlan Level Duplex Speed Type
----- ------------------ ---------- ---------- ------ ------ ----- ------------
5/1 Workstation A connected 1 normal full 100 10/100BaseTX
Port Security Secure-Src-Addr Last-Src-Addr Shutdown Trap
----- -------- ----------------- ----------------- -------- --------
5/1 disabled No disabled
Port Broadcast-Limit Broadcast-Drop
-------- --------------- --------------
5/1 - 0
Port Align-Err FCS-Err Xmit-Err Rcv-Err UnderSize
----- ---------- ---------- ---------- ---------- ---------
5/1 0 0 0 0 0
Port Single-Col Multi-Coll Late-Coll Excess-Col Carri-Sen Runts Giants
----- ---------- ---------- ---------- ---------- --------- --------- ---------
5/1 0 0 0 0 0 0 0
Last-Time-Cleared
--------------------------
Wed Jul 15 1998, 20:04:06
Cat5500> (enable)
Figure 17 Verifying VLAN port assignment on a Catalyst 5500
Suggestion #2:
Verify that trunking is enabled and functioning properly between the switches.Cat5500> (enable) show trunk
Port Mode Encapsulation Status Native vlan
-------- ----------- ------------- ------------ -----------
1/1 on isl trunking 1
1/2 on isl trunking 1
Port Vlans allowed on trunk
-------- ---------------------------------------------------------------------
1/1 1-1005
1/2 1-1005
Port Vlans allowed and active in management domain
-------- ---------------------------------------------------------------------
1/1 1-12
1/2 1-12
Port Vlans in spanning tree forwarding state and not pruned
-------- ---------------------------------------------------------------------
1/1 1-12
1/2 1-12
Cat5500> (enable)
Figure 18 Verifying trunking on a Catalyst 5500
PROBLEM:
A workstation can’t communicate with any servers or other workstations, and you are not sure which port the user is connected to, since your patch cables are not labeled.Cat5500> (enable) show cam 00-90-f2-79-f8-00
* = Static Entry. + = Permanent Entry. # = System Entry. R = Router Entry.
VLAN Dest MAC/Route Des Destination Ports or VCs / [Protocol Type]
---- ------------------ ----------------------------------------------------
1 00-10-f3-96-e7-01 7/14 [ALL]
Total Matching CAM Entries Displayed = 1
Cat5500> (enable)
Figure 19 Locate a MAC address on a Catalyst 5500
A Tour of the Cisco IOS Documentation
Once you've finished this book you'll probably want more information on individual router or switch commands, so you'll need to consult the Cisco IOS documentation.
Like all other software developers, Cisco has incorporated ever more features into the IOS over the years, until it has become difficult to find the information you need in the documentation. That's why I like to give the students in my classes an overview of how the documentation is organized.
The IOS documentation comes in several formats. You can buy the documentation for IOS 11.3 in paper form from Cisco Systems for $760. Older versions are only a little less costly. Be sure to reserve about four feet of shelf space for it in your library. You can buy individual configuration guides or command references from Cisco, if your interest in the software is limited to one or two protocol suites or technologies. Cisco Press has recently started publishing these documentation volumes for the general public, so you can get them in bookstores now, as well.
If you buy a Cisco router or switch, attend a Cisco training course, or work for a company that has a partnership with Cisco, you will have access to the documentation for all Cisco products, including all versions of IOS back to version 8.2, on CD-ROM. If you don't have the documentation CD, don't despair; anyone who can get to the Internet with a Web browser can visit the Cisco Web site and view all of the same documentation. Follow the links from the Service and Support page at www.cisco.com.
Once you pick the IOS version you want to consult, you'll want to look at the section called Configuration Guides and Command References. The documentation is organized into topics, and each topic has both a configuration guide and a command reference. When I have the paper documentation, I use the two parts side by side. The configuration guide gives you an overview of the topic, and step-by-step instructions on how to configure the router to support individual features, along with the commands you would use and the functions they perform. In the back of each section of each configuration guide you will find examples of actual router configurations. You will need to consult the command reference for the details on each command, any parameters or options you can use with it, and any warnings that pertain to it.
The topics you'll want to consult to reinforce the knowledge you've gained in this book will be "Configuration Fundamentals", "Wide Area Networking", and "Switching Services". The "Network Protocols" topics are divided into three categories. Network Protocols I has everything about configuring TCP/IP-related features, and Network Protocols II contains information on Novell IPX and AppleTalk.
Happy studying, and good luck in your certification efforts!
—By Pamela Forsyth, CCIE, CCSI, CNX
Certification Summary
VLANs provide flexibility when designing and implementing switched network infrastructures. They are closely tied to switching, and provide valuable features such as increased security, the capability to create workgroups based on functional needs, and broadcast control. The early switches simply provided increased performance over traditional hubs; the next generation of switches offered the capability to create VLANs to further increase performance and segment your network.
VLANs are part of any comprehensive network design, but you should understand your user requirements and traffic flows before implementing. Weigh the benefits of additional VLANs from a performance and administration perspective: Will additional VLANs improve performance in your network, or will they place an increased load on your routers? How will you manage these new VLANs on a day-to-day basis? Will more VLANs be easier or more complex to maintain and administer?
The Spanning-Tree Protocol was developed to eliminate redundant loops in networks, and is used in switched networks. The lack of active physical loops in your network will still provide redundancy, but you must understand the convergence time after a failure in your network. After a trunk fails, spanning tree will place your redundant port in active mode after it has ensured that there are no other loops in your topology.
Cisco switches provide VLAN 1 by default and all active ports are assigned to that VLAN. In addition, other default VLANs already defined are FDDI and Token Ring. If your network is comprised of multiple switches, you have two options for trunking this information between the switches in your network. VLAN Trunk Protocol (VTP), developed by Cisco, provides the capability to add, delete, and change VLANs from a central point of administration. You can create a VTP server switch, with all other switches being clients; or they can all be servers, capable of updating VLAN information in your network. The other option is to place your switches in transparent mode and manually configure VLANs across each switch as they are needed. Reserve time in your design process to consider the requirements for user adds, moves, and changes, as these will impact your needs for VLAN changes across your switches. If your users will move between floors and buildings, and their VLANs must follow, you should probably consider VTP. If your users will not move, or you implement a centralized server farm, transparent mode may be best. When resources are centralized on VLANs in the data center, and you use DHCP for IP addressing of workstations, a user’s VLAN location does not matter. Adds, moves, and changes are simple and are not VLAN dependent.
After you have created your VLANs, you will want to assign them to switch ports across your Catalysts. The different ways to assign ports to VLANs depends on the line cards you order for your chassis. In our examples, we configured the 24 Port 10/100 module, since each port can be configured to a separate VLAN. By default, all ports on this card are assigned to VLAN 1 when the module is installed in the chassis.
VLAN trunks are required to exchange VLAN information between switches. There are several different methods for trunking, including ISL, IEEE 802.1Q, IEEE 802.10, and LAN Emulation. ISL is a protocol developed by Cisco to exchange VLAN information between routers and switches.
VLANs allow you to design a flexible network that can easily support changing user requirements. It is important to weigh the costs of many VLANs from a support perspective. They are a part of detailed design and can provide many benefits to you and your users. Cisco switches provide the capability to add, change, and delete VLANs, as well as assign them quickly and easily.
Two-Minute Drill
![]()
The Self Test questions will help you measure your understanding of the material presented in this chapter. Read all the choices carefully, as there may be more than one correct answer. Choose all correct answers for each question.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
C. The term VLAN is most commonly associated with switches.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
![]()
![]()
![]()
B. VLAN creates a Layer 3 type network.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
D. A hub repeats all frames to all ports except the port on which the frame was received.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
B. Unicast frames are directed towards a specific MAC address.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
B. VLAN is a logical collection of end stations.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
D. Broadcast domain is independent of physical location, LAN media, and transmission rates.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
A. VLAN allows logical grouping of a workforce based on functions performed by the groups.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
C. Transparent bridging uses the spanning-tree algorithm.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
C. Transparent bridging is used primarily in Ethernet environments.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
A. True. Token Ring frames contain a RIF, whereas Ethernet frames do not contain a RIF.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
D. The RIF may contain a combination of bridge numbers and ring numbers.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
C. set vtp password and set vtp pruning enable are optional commands.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
A. The five states that a port can have are blocking, listening, learning, forwarding, disabled.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
B. The portfast option bypasses the learning and listening states.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407