GLOBAL KNOWLEDGE NETWORKä CERTIFICATION PRESS |
Chapter 2
Getting Started with Cisco IOS Software
Certification Objectives
*User and Privileged Modes
*The Command-Line Interface
*Router Elements
*Router Modes
*Examine the Router Status
*Cisco Discovery Protocol
*Remote Access to a Router
*Basic Testing
*Debug
*Routing Basics
*Path Determination
*Forwarding
*From the Classroom
*A Perspective on Passwords
*Virtual Configuration Register Settings
*Startup Sequence - Boot System Commands
*Configuring to/from a TFTP Server
*
![]()
A router needs to be configured in order to operate within your network. Once it is configured, network operators often need to check the status of various router components. In this chapter you will learn about the configurable components of a router and how to use the features of the user interface to configure the router and to verify your configuration. You will also learn how to do some basic network testing using the Cisco IOS diagnostic capabilities, and how to gain remote access to other routers over the network. Finally, you will learn several techniques for manipulating configuration files.
User Interface
The most common way to interact with the router is through the command-line interface provided by the Cisco IOS software. Every Cisco router has a console port that can be directly connected to a PC or terminal so that you can type commands at the keyboard and receive output on a terminal screen. The term "console" refers to this keyboard and screen that are directly attached to the router.
{Answer to Self Test Question #23}The part of the IOS software that provides the user interface and interprets the commands you type is called the command executive, or EXEC. {Answer to Self Test Question #21}This section will teach you how to log into the router, use the features provided by the user interface, and log out of the router again. It will also introduce the two primary modes of interacting with the router: user EXEC mode and privileged EXEC mode.
If you walk up to a router console that has been idle for some time, you will see a screen displaying the following lines.
east con0 is now available
Press RETURN to get started.
In order to begin working with the router from the console you will need to log in. If you press Enter, you will be prompted for a password.
User Access Verification
Password:
Router>
You will not see the password characters appear on the console screen.
Once you have successfully entered the console password, you will see the prompt "Router>." The router is now waiting for you to type a command at the console keyboard. "Router" is the default hostname for all Cisco routers; the angled bracket following the hostname is a signal to you that you are in user EXEC mode (user mode). This is the lowest level of access to the router, and allows you to examine the status of most of the routerís configurable components, see the contents of routing tables, and do basic non-disruptive network troubleshooting. You cannot change the routerís configuration in user EXEC mode, nor can you view the contents of the routerís configuration files.
{Answer to Self Test Question #26} You should always use this mode for interacting with the router unless you actually need to change your routerís configuration, or if you need to do disruptive testing on your network.{Answer to Self Test Question #25}
The highest level of access to the router is privileged EXEC mode, sometimes called enable mode, because the command you use to get into this mode is ENABLE. Here is what you would see at the router console as you enter privileged EXEC mode:Router>enable
Password:
Router#
Notice how the prompt changes. You can confirm you are in privileged EXEC mode by the pound sign (#) after the router name.
{Answer to Self Test Question #27} {Answer to Self Test Question #3}At this level you have full access to the router. In privileged EXEC mode, you have all the commands available for basic troubleshooting and status-checking that you had in user EXEC mode, plus commands that enable you to change the routerís configuration, perform testing that could potentially disrupt network traffic, reboot the router, and view the configuration files.To leave privileged EXEC mode and revert to user EXEC mode, use the command DISABLE.
Router#disable
Router>
Notice how the prompt changes back to the angled bracket. To log out of the router entirely and end your console session, use the command EXIT or LOGOUT.
{Answer to Self Test Question #1} Once you are logged out of the router, the console screen will once again display the idle console message instructing you to "press ENTER to get started."Letís log back into our router again and learn how to use the context-sensitive Help feature. This is a feature that you will learn to depend on as you work with the command-line interface.
If you want to know all the commands available to you at any time, just enter a question mark (?) at the prompt. Here is a partial listing of commands available in user EXEC mode.
router>?
Exec commands:
access-enable Create a temporary Access-List entry
clear Reset functions
connect Open a terminal connection
disable Turn off privileged commands
disconnect Disconnect an existing network connection
enable Turn on privileged commands
exit Exit from the EXEC
help DEscription of the interactive help system
lat Open a lat connection
lock Lock the terminal
login Log in as a particular user
logout Exit from the EXEC
mrinfo Request neighbor and version information from a multicast router
mstat Show statistics after multiple multicast traceroutes
mtrace Trace reverse multicast path from destination to source
name-connection Name an existing network connection
pad Open a X.29 PAD connection
ping Send echo messages
ppp Start IETF Point-to-Point Protocol (PPP)
resume Resume an active network connection
This display goes on for another screen or two. The "More" at the bottom of the display means that you may see the next screen of output by pressing the space bar, or see one additional line by pressing the Enter key. Any other keypress will abort the display.
Now letís get into privileged EXEC mode and see how this display differs.
Router>enable
Password:
Router#?
Exec commands:
access-enable Create a temporary Access-List entry
access-template Create a temporary Access-List entry
bfe For manual emergency modes setting
clear Reset functions
clock Manage the system clock
configure Enter configuration mode
connect Open a terminal connection
copy Copy configuration or image data
debug Debugging functions (see also 'undebug')
disable Turn off privileged commands
disconnect Disconnect an existing network connection
enable Turn on privileged commands
erase Erase flash or configuration memory
exit Exit from the EXEC
help DEscription of the interactive help system
lat Open a lat connection
lock Lock the terminal
login Log in as a particular user
logout Exit from the EXEC
mbranch Trace multicast route down tree branch
mrbranch Trace reverse multicast route up tree branch
--More--
Many commands you will be using have many parts or arguments. The command executive uses a real-time interpreter to execute the commands you type at the console, and it checks the syntax of each one for correctness as you enter it. You can use this syntax checking, along with the context-sensitive Help feature, to learn what information the router expects you to type at any point in any command. Letís look at the example command, CLOCK SET.
Router#clkTranslating "clk"...domain server (255.255.255.255) % Name lookup aborted
The first thing to notice is that I am in privileged EXEC mode here. You canít set your routerís clock from user EXEC mode. I made a mistake in typing the command. If the router sees a word it doesnít recognize as a command, it thinks you are specifying the name of an IP host you want to Telnet to over the network, and tries to resolve the hostname to an IP address.
{Answer to Self Test Question #2}If you donít have a DNS server on your network, this process takes several seconds to time out. If you want to abort the name lookup, as I did here, use the keystrokes Ctrl-Shift-6.Now I want to find out which commands begin with "cl." I can do that by typing cl?. There is no space between the "l" and the question mark.
Router#cl?
clear clock
Now I can use the question mark to find out the arguments I need to use for the CLOCK SET command. Watch the space between the last argument on the line and the question mark.
{Answer to Self Test Question #30}Router#clock ? set Set the time and dateRouter#clock set ? hh:mm:ss Current TimeRouter#clock set 17:50:00 % Incomplete command.
Router#clock set 17:50:00 ?
<1-31> Day of the month
MONTH Month of the year
Router#clock set 17:50:00 1
% Incomplete command.
Router#clock set 17:50:00 1 ?
MONTH Month of the year
Router#clock set 17:50:00 1 August
% Incomplete command.
Router#clock set 17:50:00 1 August ?
<1993-2035> Year
Router#clock set 17:50:00 1 August 1998
Router#
When I get the router prompt back again with no error message I know the command was correct in syntax.
Some of the commands you will type are very long. It is helpful to know some of the keystrokes that are available to you for moving around on the line you are working on. This feature is known as enhanced editing. If you are familiar with UNIX, you will recognize these keystrokes as the emacs editing keystrokes.
If you are using a VT-100 terminal emulation, you may use the left and right arrow keys on your keyboard to move along the line. Use the Delete and Backspace keys to change characters on the line. Once you press the Enter key, the command will take effect.
{Answer to Self Test Question #4}Enhanced editing also includes a feature that scrolls long lines to one side if they are longer than the terminal screen width. This is indicated by a $ next to the prompt, like so:
Router>$n extra long line to show how it scrolls under the router prompt
As soon as the line you are typing exceeds the width of the terminal screen, ten characters will appear to scroll under the router prompt. Use the Ctrl-A keystroke to get back quickly to the beginning of the line.
If you donít want to use the enhanced editing feature, you may turn it off with the command terminal no editing. To enable it again, use the command terminal editing.
The router keeps the last ten commands you entered during your console or terminal session in a special memory buffer called the command history.
{Answer to Self Test Question #5}You may recall commands from the command history and re-use them or change them slightly to save yourself some typing. To see all the commands in the buffer, use the SHOW HISTORY command:Router#show history conf t
show interfaces serial show interfaces show run clk clock set 17:50:00 clock set 17:50:00 1 clock set 17:50:00 1 August clock set 17:50:00 1 August 1998 show historyRouter#
Notice the commands are recalled exactly as they were typed, even if they were incomplete or erroneous.
You can recall the commands to the command line by moving backward and forward within the history buffer. Ctrl-P recalls the previous command in the buffer,
{Answer to Self Test Question #13}and Ctrl-N recalls the next command in the buffer. If your terminal is using a VT-100 emulation you can use the up and down arrow keys to move backward and forward within the buffer. Use the terminal history size command to change the size of the history buffer. For example, to increase the size of the buffer so it will store 100 lines instead of the default ten, enter the following:Router#terminal history size 100
Router#
Router Basics
A router is a computer, and has hardware elements that are similar to those of other computers. If you buy a PC from the local computer store, it will have:
A router has these same elements. In this section we will learn about the configurable hardware elements of the router, how to configure them, and how to check their status.
Before we power up the router we need to understand some of its components. The hardware components of the router include memory, processor, lines and interfaces.
The Cisco router uses the following types of memory.
{Answer to Self Test Question #31}The whole point of a router is to forward packets from one network to another, so it stands to reason that a routerís interfaces will be of primary interest to us. Interfaces are those elements that physically connect the router to various types of networks. Some of the most common router interfaces are serial (which generally connect the router to wide-area links), and the LAN interfaces: Ethernet, Token Ring, and FDDI.
The final category of router component is the one that allows us to interact with the router. We have already learned about the console port, which connects the router to a local terminal. The router also has an auxiliary port, which is often used to connect the router to a modem for out-of-band management in case the network connections are down and the console is inaccessible.
The routerís command executive has a hierarchy of modes that limit and organize the commands available to you, the user, as you configure the router. You have already learned the primary router modes, user EXEC mode and privileged EXEC mode, which can be used to check the routerís operating status and troubleshoot your network. In order to configure the router, however, we need to understand the configuration modes and how to move among them.
You cannot change the routerís configuration from user EXEC mode, so if you need to configure the router, you first must enter privileged EXEC mode.
Once you are in privileged EXEC mode, you may enter global configuration mode. This is the mode you would use to accomplish such tasks as naming your router, configuring a banner message for users logging in to the router, and enabling various routed protocols. Any configuration command that affects the operation of the entire router would be entered in global configuration mode.
Enter global configuration mode by using the command configure terminal.
Router#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#hostname MyRouter
MyRouter(config)#
Notice how the prompt changes to remind you that you are in global configuration mode, instead of privileged EXEC mode.
To exit global configuration mode and get back to privileged EXEC mode, use the command EXIT or the keystroke Ctrl-Z.
{Answer to Self Test Question #29}The commands take effect immediately when you press the Enter key, and are placed in the running configuration in RAM, which is controlling operation of the router. You can see in the preceding display that as soon as the HOSTNAME command was entered, the routerís prompt changed to reflect the new name.
{Answer to Self Test Question #16}Most users want to check their running configuration right away to see if the new command is reflected in it properly. If you want to do this, remember that you canít use any SHOW commands in global configuration mode, or in any other configuration mode for that matter. You must first exit back to privileged EXEC mode to use the SHOW commands.
Of course, you will want to configure the specific elements of your router. In order to do this you must first be in global configuration mode. All other configuration modes are entered from global configuration mode. Some of the more frequently used additional configuration modes available, with their special prompts, include:
Table 2-1 shows the most commonly used router configuration modes and how to navigate the user interface from one to another.
|
Command Mode |
Access Method |
Router Prompt |
Exit Method |
|
User EXEC |
Log in |
Router> |
Use the LOGOUT command |
|
Privileged EXEC |
From user EXEC mode; enter the ENABLE command |
Router# |
To exit to user EXEC mode, use the DISABLE, EXIT or LOGOUT command |
|
Global configuration |
From the privileged EXEC-mode, enter the configure terminal command |
Router (config)# |
To exit to the privileged EXEC mode, use the EXIT or END command. Or press Ctrl-Z |
|
Interface configuration |
From the global configuration mode, enter the INTERFACE type number command, such as interface Ethernet 0 |
Router (config-if)# |
To exit to global configuration mode, use the EXIT command. To exit directly to the privileged EXEC mode press Ctrl-z |
Table 1 Common Command Modes
From time to time, you will be called upon to examine the status of your routers. Whether it is to see if a device is alive on the network, to verify the up/down status of an interface, or determine what is causing the router to go into a slowdown. The commands we use to view the status of router elements and processes are known collectively as SHOW commands.
You will need to know the basic SHOW commands that allow you to view the elements we have just discussed. One of the more commonly used SHOW commands is the show interface command. Here is an example of this command and its result.
Router1#show interface tokenRing 1
TokenRing1 is up, line protocol is up
Hardware is TMS380, address is 0000.303a.c2cd (bia 0000.303a.c2cd)
DEscription: Lab Backbone
Internet address is 172.16.1.1/26
MTU 4464 bytes, BW 16000 Kbit, DLY 630 usec, rely 255/255, load 1/255
Encapsulation SNAP, loopback not set, keepalive set (10 sec)
ARP type: SNAP, ARP Timeout 04:00:00
Ring speed: 16 Mbps
Single ring node, Source Route Transparent Bridge capable
Source bridging enabled, srn 2699 bn 1 trn 2710 (ring group)
proxy explorers disabled, spanning explorer enabled, NetBIOS cache disabled
Group Address: 0x00000000, Functional Address: 0x0880011A
Ethernet Transit OUI: 0x000000
Last input 00:00:00, output 00:00:01, output hang never
Last clearing of "show interface" counters never
Queueing strategy: fifo
Output queue 0/40, 0 drops; input queue 0/75, 0 drops
5 minute input rate 42000 bits/sec, 11 packets/sec
5 minute output rate 1000 bits/sec, 1 packets/sec
9868965 packets input, 3658968237 bytes, 0 no buffer
Received 7911721 broadcasts, 0 runts, 0 giants, 0 throttles
0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored, 0 abort
2157045 packets output, 366298970 bytes, 0 underruns
0 output errors, 0 collisions, 0 interface resets
0 output buffer failures, 0 output buffers swapped out
0 transitions
The first line of this command is the one most often consulted to determine the status of an interface.
{Answer to Self Test Question #8} {Answer to Self Test Question #17}There are two parts to this line. The first describes the status of the physical layer components, the second of the data-link layer. An interface that is "up, up" is one that is fully operational. "TokenRing1 is up" means that the interface hardware has detected appropriate electrical signaling, or "carrier detect." If there is no carrier signal, the interface will be down, and the line would read, "TokenRing1 is down, line protocol is down."The second part of this line, "line protocol is up," means that the router is detecting keepalive messages on the ring. It is possible for a carrier signal to be present, but no keepalive messages. In this case the line would read, "TokenRing1 is up, line protocol is up."
If we wanted to turn off processing on this interface without physically connecting it to the network, we could put it in an administratively down status. If we had done this, the first line of output would read, "TokenRing1 is administratively down, line protocol is down."
Each type of physical interface, such as Ethernet or serial, has slightly different information in its show interface display that is specific to that data-link technology.
Other SHOW commands that are useful are:
Cisco Discovery Protocol (CDP) is one of the best methods of understanding your network topology. CDP is a Layer 2 media- and protocol-independent protocol that runs on all Cisco-manufactured equipment, including routers, switches, and access servers. The devices do not need to have any network layer protocols configured in order to use CDP, although if these addresses are configured, CDP will discover them.
{Answer to Self Test Question #14}Each device configured for CDP sends out periodic messages to a MAC layer multicast address. These advertisements include information about the capabilities and software version of the advertising platform. This gives you an easy way to see other Cisco devices on your network, without having to figure out which devices are Cisco by the vendor code embedded in the Media Access Control (MAC) address. {Answer to Self Test Question #41}Contents of the CDP table can be viewed with the following commands.ROUTER1#show cdp neighbor
This command shows information about Cisco devices locally attached to this device. "Locally attached" indicates that a device is either on the same LAN segment, or connected via a serial interface. Device ID is the hostname of the advertising router. The "local Intrfce" column indicates the interface on the router whose console you are at, and the "Port ID" column indicates the attached interface on the remote router.
CDP multicasts are normally sent every 30 seconds. The default holdtime is 180 seconds. The holdtime figure indicates how long this entry will continue in the routerís CDP table if no more advertisements are heard from this neighbor.
{Answer to Self Test Question #42}ROUTER1#show cdp neighbor detail
This command takes the previous command one step farther. This command will show all network layer addresses of the advertising interface, as well as the IOS version. CDP is an excellent troubleshooting tool to determine neighboring devices that could be causing problems due to misconfigured addresses.
In a large network with many remote locations it is impossible for a network administrator to gain physical console access to a router each time he needs to check its status or to change its configuration. It makes good sense to use the network itself to provide remote access to the routers in the network whenever possible. This is known as in-band management. Most often, the application used for remote access over an IP network is Telnet.
Every Cisco router has the Telnet application included in the IOS. This enables the administrator to establish a Telnet session into the router from any other IP host with Telnet capability, or to Telnet from the router itself to another router or IP host. You can perform most of the same configuration and status-checking functions from a Telnet session that you can perform from the router console.
Telnet sessions to or from the router are also called virtual terminal sessions. The router contains five virtual terminal lines (VTY lines), to accept incoming Telnet sessions. A Telnet session may be carried through any of the routerís physical interfaces, and attach to any of the routerís VTY lines.
In order for a router to accept an incoming Telnet session, at least one of its VTY lines must be configured with a password.
To initiate a Telnet session with a router, you must know an IP address of one of the interfaces in the router, or a symbolic name that can be resolved to an IP address in the router. The network must also be capable of routing the IP packets to that address; that is, the network portion of the address must be known to the routers in the internetwork that are between the host you are initiating the Telnet session from, and the target router.
The user interface presented by the Telnet application is identical to the interface at the router console, and is navigated in the same way.
Once you have established a Telnet session you may terminate it by entering the EXIT or QUIT commands. Sometimes, however, you know you will want to go back to that session, but need to get back to the router you started from for a moment. If you want to suspend your session so you can go back to it within a short period of time, use the keystrokes Ctrl-Shift-6 x. To get back to the suspended session, just press the Enter key by itself on a line.
{Answer to Self Test Question #32}The Cisco IOS software includes several commands that can be used to test basic connectivity in an IP network.
Ping is a tool that tests connectivity at the network layer only. It operates by sending a series of ICMP echo packets to the destination, and keeping track of the ICMP echo-replies that the destination sends back. You may use ping with its default characteristics (five 100-byte packets, two-second timeout) from user EXEC mode, but if you are in privileged EXEC mode, several other options become available to you. This is known as extended ping. Some of the other options available with extended ping include: varying the sizes of the packets, increasing the timeout value, sending more than five packets at one time, setting the "donít fragment" bit in the IP header, and even using ping for other protocols, such as IPX and AppleTalk.
Here is sample output of a default ping. 172.20.2.1 is the IP address of our destination host.
Router1# ping 172.20.2.1
Type Escape sequence to abort.
Sending 5, 100-byte ICMP Echoes to 172.20.2.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/15/64 ms
Router1#
The series of five exclamation points indicate the response packets received successfully by our router. A dot (period), instead of an exclamation point, indicates the request timed out, either because the ICMP echo request never reached its destination, or because the response was dropped or misrouted somewhere in the network.
Another command that tests network layer connectivity is the traceroute command. Traceroute provides information about which path your traffic is taking through the internetwork, hop by hop, as well as how long each hop is taking. Here is an example of traceroute output.
Router1>trace 10.30.30.254
Type Escape sequence to abort.Tracing the route to 10.30.30.254
1 10.2.0.2 12 msec 12 msec 12 msec
2 10.1.0.1 16 msec 12 msec 8 msec
3 10.3.0.1 60 msec 56 msec *
Router1>
Debug is a tool you can use to get detailed diagnostic information from your router about routing processes and messages the router is receiving, sending, or acting upon. The debug privileged EXEC commands can provide a wealth of information about the traffic being seen (or not seen) on an interface, error messages generated by nodes on the network, protocol-specific diagnostic packets, and other useful troubleshooting data.
Great care should be taken when using the DEBUG command. By issuing a DEBUG command, you are asking the router to not only process traffic as normal, but to report information to the console or VTY session. The amount of processing power consumed by the DEBUG command varies with the quantity of information written to the console screen, which can vary dramatically according to the size and traffic load of the network. Some DEBUG commands generate a single line of output per packet, and others generate multiple lines of output per packet. Some generate large amounts of output, and others generate only occasional output. A DEBUG command that produces a large quantity of output can be very processor intensive, and may occupy so many of the routers processor cycles that it can cause network interruptions or even cause the routerís operating system to freeze or crash.
The DEBUG command is issued from privileged EXEC mode and always requires arguments. You should use the context-sensitive Help feature to discover what they are for your particular IOS version and feature set. Always be as specific about the debug output as you can in order to avoid overburdening your router. You want the minimum volume of debug output that will give you the information you are seeking.
If you are using a VTY or Telnet session to the router, you will not see any debug output unless you use the command terminal monitor.
{Answer to Self Test Question #12}By default, debug output will only appear on the console screen.Always remember to use the no debug or undebug all command to disable the debug output as soon as you are finished. See the following example of a debug output for an IGRP routing update being broadcast on several interfaces:
Router# debug ip igrp events
IGRP: sending update to 255.255.255.255 via Ethernet0 (172.16.1.1)
IGRP: Update contains 104 interior, 0 system, and 0 exterior routes.
IGRP: Total routes in update: 104
IGRP: Update contains 62 interior, 42 system, and 0 exterior routes.
IGRP: Total routes in update: 104
IGRP: Update contains 0 interior, 57 system, and 0 exterior routes.
IGRP: Total routes in update: 57
IGRP: sending update to 255.255.255.255 via TokenRing1 (172.17.1.1)
IGRP: Update contains 1 interior, 3 system, and 0 exterior routes.
IGRP: Total routes in update: 4
IGRP: sending update to 255.255.255.255 via TokenRing1 (192.168.23.10)
IGRP: Update contains 0 interior, 0 system, and 0 exterior routes.
IGRP: Total routes in update: 0 - suppressing null update
So as you can see, DEBUG can be a very powerful tool to determine problems with your network. But keep in mind that you can cause serious network outages if you are not careful!
Routers perform two basic functions: path determination and packet forwarding. The basic purpose of a router is to move information from one place to another. No matter what your protocol isóIP, IPX, AppleTalk, DECnet, or Vinesóthe purpose of the router does not change. It will perform the packet-forwarding function in the same way. When it receives a packet it will consult its routing table for that protocol to find the next-hop address that will get the packet toward its destination, and forward the packet out the interface toward that next hop.
A multiprotocol router maintains a separate routing table for each routed protocol. A routed protocol is a protocol that is used to carry user data, such as IPX or TCP/IP. A routing protocol is used only by the routers to tell each other what networks they know how to reach. A routing protocol is rarely used by host computers on a network. Routing protocols assist in the path-determination function by allowing the router to learn dynamically about the topology of the internetwork.
Routers use routing protocols to build and maintain routing tables and to forward data packets along the best path toward their destination networks. Routing protocols enable routers to learn about the status of networks that are not directly connected to them, and to communicate to other routers about the networks they are aware of. This communication is carried out on a continual basis, so the information in the routing table is updated as changes occur in the internetwork.
Routers that are neighbors on a link need to use the same routing protocol to communicate so that they can learn each otherís routes and in turn, communicate them to other neighboring routers. More than one routing protocol can be operational within a single router, although this is a practice you should avoid in designing your network, because it requires extreme care in the configuration.
The characteristics that distinguish one routing protocol from another include:
There are two basic categories of routing protocols: distance vector and link-state.
Routers configured with a distance vector protocol use frequent broadcasts of their entire routing tables on all their interfaces in order to communicate with neighboring routers. The more routes in their routing tables, the more routes that are broadcast. This limits the size of network that can use a distance vector routing protocol efficiently. The metric (measure of preferability) of one link or path when compared to another, is usually hop count. The hop count increases by one each time a packet must transit a router.
Look at Figure 2-1 to see how distance vector protocols propagate routes through the network and build their routing tables. The routing tables contain: identifiers for the individual networks, an interface within the router through which the router learned about that network, and the number of hops away the network is. "C" stands for "directly-connected."
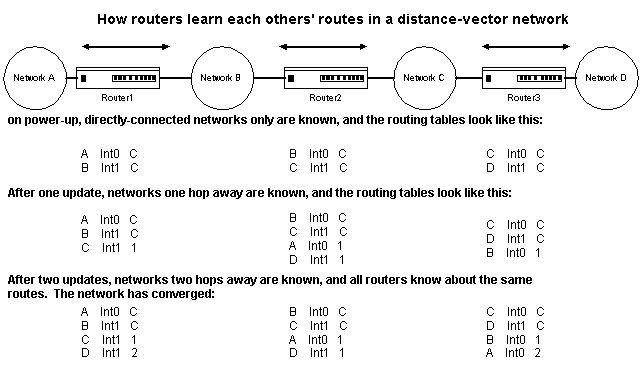
Figure 1 Routing table development in a distance vector environment
Notice that it takes two updates for all the routers to contain the same networks in their routing tables. When this has happened, the network is said to have converged. The time it takes for convergence to occur after a change in network topology is called convergence time.
The advantage of distance vector protocols is their extreme simplicity. Hop count metrics are easy to administer, and the distance vector protocols usually come with very few configurable parameters for tuning purposes.
The disadvantage is that hop count metrics make every link look the same, whether it is a 622-Mbps Sonet ring or a 1.544-Mbps T-1 line.
Consider Figure 2-2. If we are using a classic distance vector routing protocol to make our path determination for us, the lower path over the T-1 link will look preferable, because it is only one hop. The upper path, even though the bandwidth is about 400 times as high, will not look as good, because it takes two hops to get from Router1 to Router2.
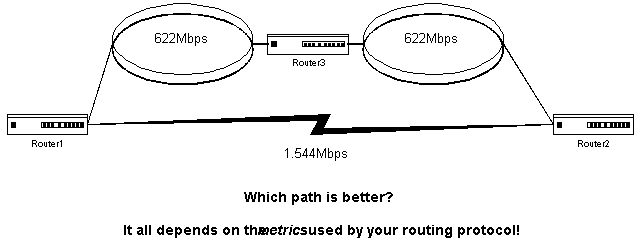
Figure 2 Different metrics allow for different routing decisions
A link-state routing protocol can usually take bandwidth into account, because it uses a cost metric, which is inherently more sophisticated. Most cost metrics are based on factors such as bandwidth or delay. This enables the link-state protocol to make better routing decisions. {Answer to Self Test Question #33}It is also more efficient in terms of its bandwidth use for updates, because link-state protocols send out their updates only when a change occurs in the network.
Link-state protocols discover their neighboring routers by using a "hello" protocol, and keep track of the updates and hellos received from their neighbors. Link-state updates are usually acknowledged, so there is no need for sending out the same information again.
Convergence usually happens quickly in a link-state network, because updates are flooded immediately through the network, and are sourced by the router directly connected to the link that has changed. There is no need for each router to wait for a periodic update to transmit the new information to its neighbor.
This process is basically the same for all protocols. In most cases, a host device (PC or server) determines that it must send a packet to another host. Having acquired a gateway router's address by some means, the source host sends a packet addressed specifically to a router's physical MAC layer address, but with the protocol (network layer) address of the destination host.
On examining the packet's destination protocol address (as you recall, Layer 3) the router determines that it either knows or does not know how to forward the packet to the next hop. If the router does not know how to forward the packet, it will drop the packet. If the router knows how to forward the packet, it changes the destination physical address to that of the next hop, and transmits the packet.
The next hop may or may not be the ultimate destination host. If not, the next hop is usually another router, which executes the same switching decision process. As the packet moves through the internetwork, its physical address changes but its protocol address remains constant
Once a packet is routed to the destination, it must be placed on the LAN segment for which it was intended. The router will at that point repeat the same process as the host did before the packet was sent. The router will determine the destination hostís MAC layer address. The router will then place that hostís MAC address on the packet and forward it.
The key is that no matter what your routed protocol is, or what your routing protocol is, the routers each make independent forwarding decisions based on the routing information stored in their routing tables. The routers forward packets on a hop-by-hop basis, one step at a time.
Initial Configuration
When you power up your router, it first needs to test its hardware, including memory and interfaces. The next step in the sequence is to find and load an IOS imageóthe operating system for the router. Finally, before the router can function properly in your network, it needs to find its configuration information and apply it. {Answer to Self Test Question #34}
If you are at the router console when it is powered on you should see something similar to the following:
System Bootstrap, Version 5.1(1) [daveu 1], RELEASE SOFTWARE (fc1)
Copyright (c) 1994 by cisco Systems, Inc. C4500 processor with 32768 Kbytes of main memory
At this point the router has loaded the bootstrap program from ROM. Next, it will load its IOS image from Flash. It first verifies the file integrity, then decompresses the image as it loads into RAM. These processes are represented by "Rs" and "#s".
Booting yj11120n from flash memory RRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRR RRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRR
[OK - 1337256/3532618 bytes] ######################################################################################################################################################################################################################################################################################### F3: 1926336+46904+183152 at 0x12000
Next we see some copyright notices and other information about the software and its features.
Restricted Rights Legend
Use, duplication, or disclosure by the Government is subject to restrictions as set forth in subparagraph (c) of the Commercial Computer Software - Restricted Rights clause at FAR sec. 52.227-19 and subparagraph (c) (1) (ii) of the Rights in Technical Data and Computer Software clause at DFARS sec. 252.227-7013. cisco Systems, Inc. 170 West Tasman Drive San Jose, California 94134-1706 Cisco Internetwork Operating System Software IOS (tm) 4500 Software (C4500-AJ-M), Version 11.1(2) Copyright (c) 1986-1996 by cisco Systems, Inc. Compiled Mon 24-May-96 22:46 [mikehub 107] cisco 4500 (R4K) processor (revision 0x00) with 32768K/4096K bytes of memory. Processor ID 01242622 R4600 processor, Implementation 32, Revision 1.0 G.703/E1 software, Version 1.0 Bridging software. SuperLAT software (copyright 1990 by Meridian Technology Corp). X.25 software, Version 2.0, NET2, BFE and GOSIP compliant. TN3270 Emulation software (copyright 1994 by TGV Inc.).
Next, the router inventories and tests its interfaces. Because most of the Cisco routers come in a variety of hardware configurations, the software must be able to detect what particular interfaces are present in the router when it powers up.
2 Ethernet/IEEE 802.3 interfaces.
2 Token Ring/IEEE 802.5 interfaces. 4 ISDN Basic Rate interfaces. 2 Serial network interfaces. 128K bytes of non-volatile configuration memory. 8192K bytes of processor board System Flash (Read/Write) 4096K bytes of processor board Boot Flash (Read/Write) Notice: NVRAM invalid, possibly due to write erase. --- System Configuration Dialog --- At any point you may enter a question mark '?' for help. Refer to the 'Getting Started' Guide for additional help. Use Ctrl-c to abort configuration dialog at any prompt. Default settings are in square brackets '[]'. Would you like to enter the initial configuration dialog? [yes]:
If the router does not find a configuration file in NVRAM and is not configured to look for one on the network, it will begin the setup dialog. The nice thing is that this is menu driven; all you have to do is answer the questions. When you are asked, "
Would you like to enter the initial configuration dialog?", if you answer no you will enter the normal operating mode. A yes answer will take you through the menu.
The setup dialog allows you to get your router running with a very basic configuration. It will allow you to name your router, set an enable password and enable secret, enable any of the network layer protocols and assign appropriate addresses to router interfaces, and enable dynamic routing protocols. You will want to check the configuration file produced by this process in order to refine the configuration.
It is easy for students to be confused about how passwords are used in the Cisco routers, and what the implications are for setting or not setting them.
Your router needs at least four passwords set for minimal security: an enable password, a console password, an auxiliary line password, and a VTY password. Unless you have configured the router to refer to a separate authentication server for this function, passwords are stored in the routerís configuration file. They can be encrypted or stored in clear text, depending on your security environment.
The primary password for router security is the enable password. This password controls access to privileged mode in your router, which allows the user to make configuration changes and do testing that could potentially disrupt network operations. By default, the enable password is not encrypted as it is stored in the configuration file.
You may have noticed during the section on the setup dialog that you are prompted for an "enable secret." The enable secret, if you have set one, overrides the enable password, and is always stored encrypted in the routerís configuration. So if you have set an enable secret, the enable password will not be used unless your router boots from an old software version (possibly stored in ROM or on a network TFTP server) that does not recognize the enable secret. It is considered a bad idea to set the enable password the same as the enable secret. This eliminates the very security benefit the enable secret is designed to provide.
By default, the router requires that passwords be set on the VTY lines in order to use them for incoming Telnet sessions. If you donít set a password on your VTY lines and try to Telnet into the router, you will get an error message, "password required but none set." If you need those Telnet sessions for remote management, be sure to set a VTY password! If you are working in a lab environment and donít want to type in a password each time you Telnet to a router, remove the "login" command under the VTY line configuration. This will eliminate the requirement for this password.
The default router configuration does not require passwords on the auxiliary or console lines. If you want to require passwords on these lines, you must not only set a password on them but also configure a "login" command on them. Without the "login" command, the password prompt will not appear and your password will be ignored.
In a lab or classroom environment you may choose not to set an enable password (or enable secret), but that isnít a good idea. If you donít set an enable password (or enable secret), the only connection from which you can get into privileged mode will be the console. That means that if you try to connect through the aux port or through a Telnet session, you wonít have any access to privileged mode if you havenít set that enable password. There are situations in which you can be essentially locked out of the router without this password setóit has happened to me.
Cisco offers an encryption service for those passwords that normally would appear in clear text in the configuration file (not the enable secret). You can turn this on at the console by using the command, service password-encryption. Once you enter this command, each password you configure will be stored in encrypted form and cannot be recovered without a password-cracking program. This is useful if your configuration files are stored on a TFTP server; it will prevent a casual observer from determining your router passwords. It is not considered to be strong encryption, however, and will not discourage a determined hacker who wishes to break into your network.
Cisco uses the MD5 algorithm to encrypt the enable secret. There is no known way to reverse this algorithm. If you use the enable secret you will not be able to use the normal techniques for password recovery, which depend on viewing the password in clear text within the startup configuration file. You will need to reset the password, because there is no way to recover it.
óBy Pamela Forsyth, CCIE, CCSI, CNX
Virtual Configuration Register Settings
{Answer to Self Test Question #35}
Every Cisco router has a 16-bit configuration register, which is stored in a special memory location in NVRAM. {Answer to Self Test Question #43} This register controls a number of functions, some of which are listed below:The configuration register boot field is the portion of the configuration register that determines whether the router loads an IOS image, and if so, where to get this image from. The least significant four bits, bits 0 through 3, of the configuration register make up the boot field
.{Answer to Self Test Question #9}If the boot field value is 0x0 (all four bits set to zeros), the router will enter ROM monitor mode.
If the boot field value is 0x1 (binary 0001), the router will boot from the image in ROM.
{Answer to Self Test Question #10}If the boot field value is 0x2 through 0xF (binary 0010 through 1111) the router will follow the normal boot sequence, and will look for boot system commands in the configuration file in NVRAM.
Enter the show version EXEC command to display the configuration register value currently in effect, and the value that will be used at the next reload. The value will be displayed on the last line of the screen display
{Answer to Self Test Question #11}as in the following example:ROUTER1#show version
Cisco Internetwork Operating System Software
IOS (tm) 4500 Software (C4500-JS-M), Version 11.2(7a)P, SHARED PLATFORM, RELEASE SOFTWARE (fc1)
Copyright (c) 1986-1997 by cisco Systems, Inc.
Compiled Wed 02-Jul-97 05:32 by ccai
Image text-base: 0x60008900, data-base: 0x60820000
ROM: System Bootstrap, Version 5.3(16) [richardd 16], RELEASE SOFTWARE (fc1)
BOOTFLASH: 4500 Software (C4500-BOOT-M), Version 11.1(7), RELEASE SOFTWARE (fc2)
ROUTER1 uptime is 12 weeks, 6 days, 10 hours, 30 minutes
System restarted by power-on at 01:09:36 Central Sun Apr 5 1998
System image file is "flash:c4500-js-mz.112-7a.P", booted via flash
Network configuration file is "pcmdiAAAa006h_162", booted via tftp from 172.16.1.1
cisco 4700 (R4K) processor (revision F) with 32768K/4096K bytes of memory.
Processor board ID 06755819
R4700 processor, Implementation 33, Revision 1.0 (512KB Level 2 Cache)
G.703/E1 software, Version 1.0.
Bridging software.
SuperLAT software copyright 1990 by Meridian Technology Corp).
X.25 software, Version 2.0, NET2, BFE and GOSIP compliant.
TN3270 Emulation software.
2 Token Ring/IEEE 802.5 interface
4 Serial network interface
128K bytes of non-volatile configuration memory.
8192K bytes of processor board System flash (Read/Write)
4096K bytes of processor board Boot flash (Read/Write)
Startup Sequence - Boot System Commands
You can place special commands in the routerís configuration file that will instruct it where to look for its IOS image. The router will scan these entries and try to execute them in sequence when it boots up. This provides you with several fallback options in case the routerís flash memory becomes corrupted. These are called boot system commands.
Usually you will want the router to boot from flash memory. The boot system command for this is:
Router1(config)# boot system flash
If you do not specify a filename, the router loads the first valid file it finds in flash memory.
In most cases you will want the router to find a backup IOS image on a TFTP server somewhere in your network if it cannot find and load an image from Flash memory. The command to designate this is:
{Answer to Self Test Question #37}Router1(config)# boot system tftp 172.16.1.150
You may wish to have more than one TFTP server on your network that stores your backup IOS images. You may have as many "boot system TFTP" commands as you like in your router configuration for redundancy.
Router1(config)# boot system rom
This command boots the router from ROM. This is a last resort, just to get the router running so you can diagnose the problem. The system image in ROM will not have as many features and capabilities as the full IOS version in Flash, so your router may not operate in a predictable way if it boots from ROM.
Be very careful of the order in which these commands are entered into the router.
{Answer to Self Test Question #36} For best results you will need to enter the boot system flash prior to the boot system rom. If the ROM command is entered prior to the FLASH command; the router will reload IOS from ROM and not from Flash. That boot system ROM command is very useful to ensure that if the Flash image is corrupted in any way, the router will come back onlineóin a limited mode, but back online to allow you to download another IOS image.Configuring to/from a TFTP Server
The router also has the capability to copy its configuration to and from a TFTP server. This gives the network administrator the ability to store configurations out to a server for configuration tracking, change auditing, or distress recovery. You will need to store your configuration on a TFTP server if it is larger than 32,000 bytes, which is the largest configuration that can fit into NVRAM. When you TFTP a configuration to the router, you can place it in Flash, NVRAM, or RAM memory. When you place the configuration into Flash, you will still need to place it into NVRAM or RAM in order for the router to be able to use it. The COPY TFTP commands can be done via either the console or a VTY session.
The commands for copying configuration files to and from TFTP servers are as follows:
Before you try to TFTP your configuration, be sure to verify that you can reach your TFTP server. Itís not going to do you much good to try and TFTP a file to or from server that is offline.
{Answer to Self Test Question #38}The PING command is useful for verifying that your TFTP server can communicate with your router.If the ping fails, verify that you have the correct IP address for the server and that the server is active (powered on), and repeat the PING command. Always remember to back up your work! Prior to downloading a new IOS or configuration file, copy the existing one in the router to the TFTP server. It is also a good idea to go to the TFTP server (or Telnet to it) and verify the exact filename as it exists on the server.
You may also change or upgrade your routerís IOS image by copying a new file from a TFTP server, or back up your routerís current image by copying it to a TFTP server. The following output shows the process of copying an IOS image from the routerís Flash memory to a TFTP server.
{Answer to Self Test Question #40}Router1# copy flash tftp c4500-js-mz.111-17a.P
IP address of remote host [255.255.255.255]? 172.20.2.1
Name of file to copy []? c4500-js-mz.111-17a.P
writing c4500-js-mz.111-17a.P !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
Router1#
You may also copy an IOS image from a TFTP server into the routerís flash memory. This is accomplished by the command COPY TFTP FLASH.
Router1(config)#copy tftp flash
File name/status c4500-js-mz.111-17a.P
[123816/2097152 bytes free/total
IP address or name of remote host [255.255.255.255]? 172.20.2.1
Name of file to copy ? c4500-js-mz.112-7a.P
Copy c4500-js-mz.112-7a.P from 172.20.2.1 into Flash address space ? [confirm]<Return>
123752 bytes available for writing without erasure.
Erase Flash address space before writing? [confirm] <Return>
bank 0...zzzzzzzzzzzzzzzzvvvvvvvvvvvvvvvveeeeeeeeeeeeeeee
bank 1...zzzzzzzzzzzzzzzzvvvvvvvvvvvvvvvveeeeeeeeeeeeeeee
Loading from 172.20.2.1: !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! [OK - 1337256/2097088 bytes]
Verify checksum...vvvvvvvvvvvvvvvvvvvvVerification successful:
Length = 1337256, checksum = 0x5A1C
You are prompted for the filename of the image you want to copy. This name is case sensitive, so it pays to verify the exact name on the TFTP server. You will then be prompted for the IP address of the TFTP server. The router will verify the amount of free space in Flash memory, and will ask you if you want to erase the existing file in flash before copying the new one. Once Flash is erased, the router will load the new file from the TFTP server. Each exclamation point in the display signifies a block of the file successfully loaded. Finally the router will verify the integrity of the complete file.
Caution: do not make any typographical errors using the copy tftp flash command when you specify the filename of the system software image you are copying. If you type a filename that does not exist when using the copy tftp flash command, then tell the system to erase the current image, the router erases the existing image in Flash memory.
{Answer to Self Test Question #39}If this happens, the router still has a working image in RAM, so your router will still function. If you think you have tried to load a nonexistent file, do not reboot the router! If you do, your router will not have a functional image in Flash memory. To recover from the accidental Flash memory erasure, execute the copy tftp flash command again to load the appropriate image into Flash memory.Autoinstalling Configuration Data
The AutoInstall process is designed to configure the router automatically after connection to your wide-area network (WAN). For AutoInstall to work properly, a Transmission Control Protocol/Internet Protocol (TCP/IP) host on your network must be running as a TFTP server, and preconfigured to provide the required configuration files. The TCP/IP host can exist anywhere on the network, as long as the following two conditions are maintained:
Your system administrator at the site where the TCP/IP host is located coordinates this functionality. You should not attempt to use AutoInstall unless the required files have been provided on the TCP/IP host. See the appropriate software configuration publications for information on how AutoInstall works.
Use the following procedure to prepare your router for the AutoInstall process:
The router will load the operating system image from Flash memory. If the remote end of the WAN connection is connected and properly configured, the AutoInstall process will begin.
If the AutoInstall process completes successfully, you might want to write the configuration data to the router's NVRAM. Perform the following step to complete this task:
copy running-config startup-config
Taking this step saves the configuration settings that the AutoInstall process created in the router. If you fail to do this, your configuration will be lost the next time you reload the router.
Certification Summary
The Cisco routerís user interface is a command-line interface. Router modes limit and organize the commands that are available to the user. The lowest level of access to the router is user EXEC mode, in which the user can verify router status and perform basic troubleshooting. The highest level of access is privileged EXEC mode, in which the user can change the routerís configuration and perform extensive network testing and diagnostics. The command to enter privileged EXEC mode is ENABLE. Context-sensitive Help and advanced editing features facilitate configuration and verification tasks.
The routerís configurable elements include memory (RAM, ROM, Flash, and NVRAM), interfaces for connecting to networks, and ports for user access and configuration. SHOW commands allow the user to verify the status or view the contents of these elements in an operational router.
Router modes allowing for configuration changes include global configuration mode, interface configuration mode, line configuration mode, and router configuration mode.
Cisco Discovery Protocol (CDP) allows Cisco devices to discover each other in the network regardless of whether they have network layer protocols configured. Telnet can be used to gain remote access to routers over the network. Ping and traceroute are useful to test network layer connectivity. Debug allows the user to get detailed information about almost every aspect of the routerís operation, although it must be used with great care to prevent overburdening the router.
Dynamic routing protocols can be categorized as either distance vector or link-state. Distance vector routers broadcast their entire routing tables periodically to each other. Link-state routers keep track of their neighbors, and flood updates through the network only when changes occur. Convergence is a state in which all routers in the network have a consistent view of the network topology.
When a router first powers up, it tests its hardware, locates and loads an IOS image, and applies configuration information. The startup sequence is controlled by the lowest four bits in the configuration registeróthe boot field. The boot field is used in conjunction with boot system commands in the configuration file to tell the router where to find its configuration information and its IOS image.
If a router does not find a valid configuration file when it boots up, it will enter the setup dialog. The setup dialog can be used to create a basic configuration for your router.
In a WAN environment, a new router can get its configuration information automatically from a TFTP server on the network. This facilitates configuration of routers at remote sites.
Two-Minute Drill
The following Self Test questions will help you measure your understanding of the material presented in this chapter. Read all the choices carefully, as there may be more than one correct answer. Choose all correct answers for each question.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
A. The boot field is the lowest four bits of the configuration register.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
D. The boot field set to 0x1 will cause the router to boot from ROM.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
False. CDP will multicast to a functional MAC address. There is no need to have any network layer address assigned to the interface to get the CDP messages to go out.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
C. The commands you enter take effect immediately, as soon as you press the Enter key.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
B. You would use SHOW FLASH to view the name of the filename in Flash memory.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
B. False. Changes to the router configuration are not allowed from the user EXEC mode.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
C. The routerís prompt will end with a pound sign (#) in privileged EXEC mode.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
B. The memory types are RAM, ROM, Flash Memory, and NVRAM.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
A. The configuration register has 16 bits.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
A. Contents of Flash memory will be copied to file2660, which is in the TFTP server.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
C. The command show cdp neighbor detail will show the IOS version.
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407
CCNA Routing and Switching Study Guide: Self Test for Exam 640-407